
Before the holidays, I was running into an odd problem with my new iMac, and when I mean “odd”, I mean that it was acting as if someone was trying to access my Mac from somewhere else. Now, I’m one of those people who always enables the OS X firewall, so the chances of a hacker attack actually occurring were probably pretty slim. But after a few days of perplexing symptoms I decided I’d better see whether someone or something was actually attempting an attack. To do this, I watched the OS X firewall log to see what was happening each time the symptoms occurred. Here’s how to do the same if you’re feeling as paranoid as I was…
OS X Firewall
To start with, what’s a firewall? Simply stated, it’s an application that closes all or specific internet protocol (IP) ports on your internet connection, allowing only incoming connections that are necessary to the regular operation of your Mac. For example, things like email, information coming into a web browser via the http protocol, and video streaming connections all have specific ports assigned to them, and your Mac — even with the firewall turned on — lets those services work normally.
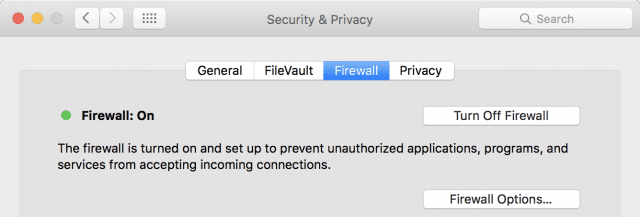
To enable the OS X firewall, go to System Preferences > Security & Privacy and then click on the Firewall tab. You’ll know immediately if the firewall is turned on or not; if it’s on, there’s a green light and a text notification that the firewall is on (see image below).
 Security & Privacy ” width=”640″ height=”217″>
Security & Privacy ” width=”640″ height=”217″>
If it isn’t enabled and you’d like to turn it on, simply click the Turn On Firewall button that is in the same location as the Turn Off Firewall button in the image. You shouldn’t need to change options for the firewall, but if you do, there’s a Firewall Options button for just that purpose. Clicking it displays something similar to the following:
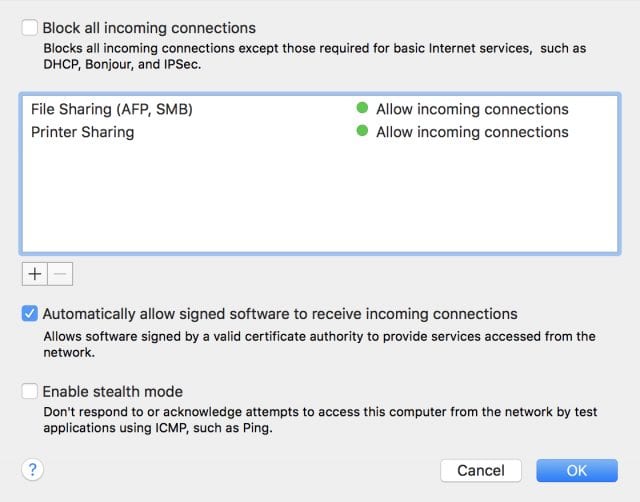
You can choose to block all incoming connections, which provides the highest level of security from intruders, just by checking the top checkbox. You can add specific applications to the “open” connection list by clicking the plus ” + ” sign below the list of allowed connections, then selecting the apps from your Applications folder. The second check box allows software that is signed by a valid certificate authority to provide services to your computer (this should be checked), and the last check box makes it impossible for malicious users to even know that your computer exists by turning off responses to test applications that make use of ICMP (Internet Control Message Protocol).
At this point, let’s assume that your OS X firewall has been enabled since you first turned on the computer and you’re still seeing some odd things happening. Your next step is to look at the OS X firewall log, and there are two different ways to do that.
View the Firewall Log in Console
The Console utility in OS X is used to view log files that are created by most system services for the purposes of troubleshooting problems. It can be found in the Utilities folder that’s located in the Applications folder, or easily accessed from the Finder by selecting Go > Utilities.
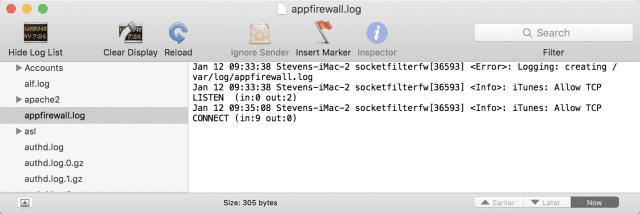
Once you’ve launched Console, go to the left sidebar of the app, look under Files, and then find appfirewall.log under /var/log. Clicking on that log file displays a list of all actions that have occurred. The following image shows a fairly clean log file, with just the iTunes app “listening” and “connecting” through the firewall:
What you want to look for are repeated blocked attempts from or to specific apps or services on your Mac. In addition, if you see connections that are taking place with an app or service you’re not familiar with or do not have installed, you might have cause for concern.
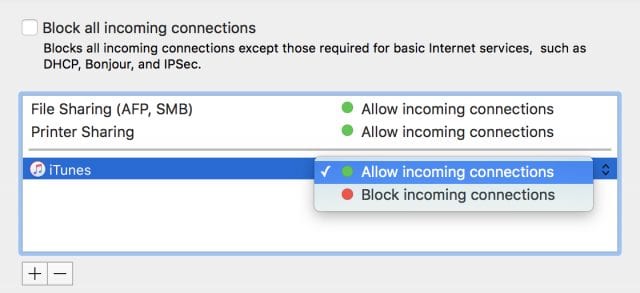
To see whether that service or app is indeed causing the issue that you’re experiencing with your Mac, see if you can find it in the list of allowed connections in the Firewall settings and then click on the toggle on the far right of the list (see image below). Select “Block incoming connections” to see if the problem is resolved. You may need to do this for various apps or services listed in the firewall connections list.
View the Firewall Log in Real Time in Terminal
If things are really getting weird, you can always choose to watch the firewall log in real time in the Terminal app. It’s also found in Applications > Utilities. Once launched, type in the following command:
tail -f /var/log/appfirewall.log
That command lists the entire firewall log up to this point in time, then lists any new entries as they are added (see image below). This is very useful in identifying apps that are constantly attempting to connect and disconnect.
If you’re not familiar with Terminal, note that you will need to type Control-C to quit the live logging and then type exit to log out of the terminal session.
Fortunately for me, all of my troubleshooting was for naught, as I found out that it was a setup issue with my Wi-Fi router that was causing the odd problems I was seeing. But it’s always worth knowing a few tricks that may help you in the future.
Be sure to check out the Rocket Yard’s Tech Tips section for more tips and tricks for OS X and iOS.















I would be interested in knowing more about what the weirdness was that caught your attention in the first place. What was happening (and by inference, should I be looking for these things on my system)?
Nice to have but so primitive compared to NetBarrier or VirusBarrier x6. Would it have broken the bank for Apple to have put in a view in the preferences panel that was nicer than the coyote ugly log? What happen to software excellence at Apple?
@Wm. Cerniuk – …I suspect that putting this into the preference panel would not only confuse most people but would not mean anything either… and to look into the terminal is not only easy but prefered for most techs who understand Unix/Linux – the distant past doing anything via the command line was the only way to do anything – the Gui allows most people easy access to what they will need in a day to day basis… most people don’t need terminal day to day nor would they understand it. As you know using the command line incorrectly can muck the system up, I don’t need to tell you this…
In my experience Intego’s netbarrier pretty much does nothing and does not stop anything – using linux a professional tech I know broke through netbarrier really easy – netbarrier not only did not stop the intrusion but also did not see the intrusions happing in real time…
We were contracted with a business who used only Mac’s, with the company you referenced, full suite (firewalls on) and their network was seriously compromised and all their systems had snoops stealing info. Using both terminal and a couple other security utilities we could see how compromised the systems were. Netbarrier did nothing to stop this. We ended up having to do a bare metal wipe and re-install with a different security suite…
…course, what did not help was the user’s passwords were terribly easy to break too – that old problem…