
In this article, we’ll show you how to spoof a MAC address on a macOS computer running High Sierra. This is a technique for changing the factory-assigned physical Media Access Control (MAC) address of a network interface on a networked device to a random address. MAC spoofing means that you’re changing a computer’s identity and it can be done for a number of reasons.
First, some Internet Service Providers (ISPs) want to register a client computer’s MAC address for service and billing services. When you wish to connect a new device to your network, the ISP may not grant access to a device with a different MAC address than those already registered to the ISP. By spoofing the MAC address to the address that was registered by the ISP, a user can work around the ISP limitation.
Next, some software can only be installed and run on systems with a pre-defined MAC address. Should you need to run that software on a new Mac or one in which the Wi-Fi (or Ethernet) card has been replaced, spoofing is required in order to make the software believe you’re using the original computer.
The primary reason for MAC spoofing is to mask your identity. In other words, this is used to protect your privacy. If you do not wish to have your computer tracked by MAC address, spoofing can show a different MAC address every time you log onto a network.
It’s interesting to note that iOS automatically delivers a random MAC address to Wi-Fi networks exactly for the purpose of preventing user tracking. This change was made to iOS by Apple in 2014.
The following instructions assume that you have some knowledge of and experience with the macOS Terminal app. If you feel uncomfortable using Terminal, then you may wish to either pass on spoofing your MAC address or use the WiFiSpoof app outlined at the end of this post. Now, let’s get to work:
1) Determine the name of the Wi-Fi interface on your Mac
Depending on the Mac you’re using, the Wi-Fi interface can have one of several names, usually en0 or en1. To figure out the address for your Mac, hold down the Option key and click on the Wi-Fi icon in the menu bar. You’ll see something similar to this screenshot:
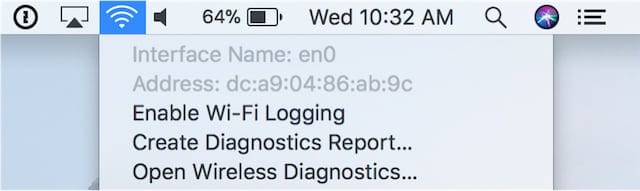
In this case, we see that the name is en0 (that’s en, followed by a zero). Remember, this may be different on your Mac.
2) Temporarily disable Wi-Fi
When spoofing the MAC address on our Mac, Wi-Fi must be temporarily disabled. This is quickly done by once again holding down the Option key, clicking on the Wi-Fi icon in the menu bar, then select “Disconnect from XYZ” where XYZ is actually the name of your Wi-Fi network (see screenshot below). You’ll get a visual indication that you’re no longer connected to the Wi-Fi network as the Wi-Fi icon becomes grayed out.
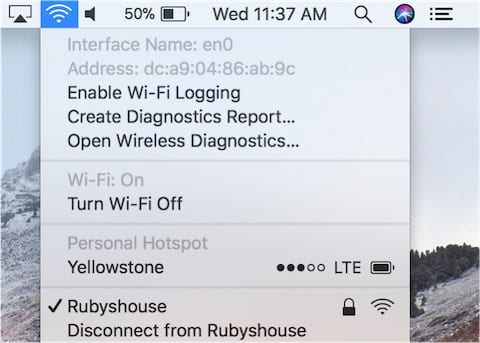
3) Launch Terminal
Next, launch the Terminal app. It’s found in the Utilities folder inside the Applications folder, or you can click on the Spotlight “magnifying glass” icon in the menu bar, type Terminal into the Spotlight search field, and press Return.
4) Verify the existing MAC address
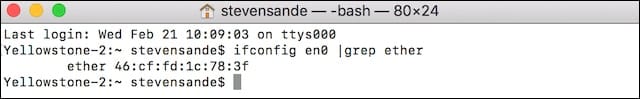
To verify the existing built-in MAC address for the Wi-Fi adapter, type the following command into Terminal and press Return:
ifconfig en0 |grep etherRemember to replace the en0 in the command with the proper name for your Mac (perhaps en1) if you determined in Step 1 that it was different from en0. In the example below, the physical MAC address is 46:cf:fd:1c:78:3f :
5) Generate a random hexadecimal number to serve as the “new” MAC address
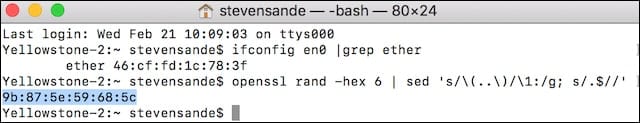
In Terminal, enter the following command (it’s OK to copy this and paste it into Terminal):
openssl rand -hex 6 | sed 's/\(..\)/\1:/g; s/.$//'The response will be a 6 hexadecimal character address. In the example below, the random address is 9b:87:5e:59:68:5c —
6) Copy the random address from Terminal, then type the following command and paste the random address at the end before pressing Return:
sudo ifconfig en0 etherIn the example below, I’ve entered sudo ifconfig en0 ether 9b:87:5e:59:68:5c
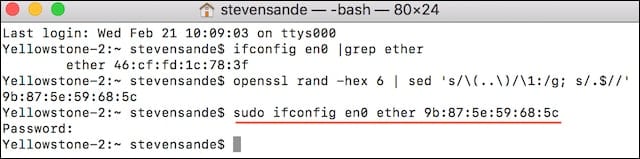
Since we’re entering this command as root, we are prompted to enter the root password.
7) Test that the random address is now our MAC address.
Once again, we’ll use ifconfig in Terminal to see what our existing MAC address is for Wi-Fi. Enter the following command:
ifconfig en0 |grep etherand we see the response as seen in the screenshot below with our random address:
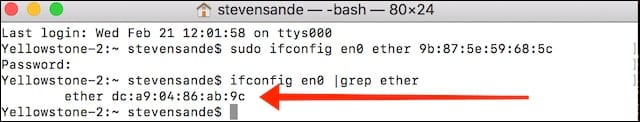
Indicating that we’re spoofing the MAC address. Success!
You can now connect to Wi-Fi again, knowing that any Wi-Fi router you’re connected to now thinks that you’re coming from another MAC address. Note that if you use the Option – Wi-Fi icon method described in Step 1, you’ll still see the physical MAC address listed, but using Terminal and ifconfig as in Step 7 will verify that the MAC address is being spoofed.
Note that when you restart your Mac, all Wi-Fi MAC address spoofing goes away — you’re back to using your physical MAC address. If you want to use the Internet anonymously all the time, spoofing your MAC address using the Terminal method can be time-consuming. Fortunately, there’s an app for that…
WiFiSpoof
For many people, MAC spoofing isn’t really necessary except on rare occasions. But for those who need to zealously protect their privacy, an app called WiFiSpoof (US$19.99, on the Mac App Store) is a quick and easy way to change a MAC address.
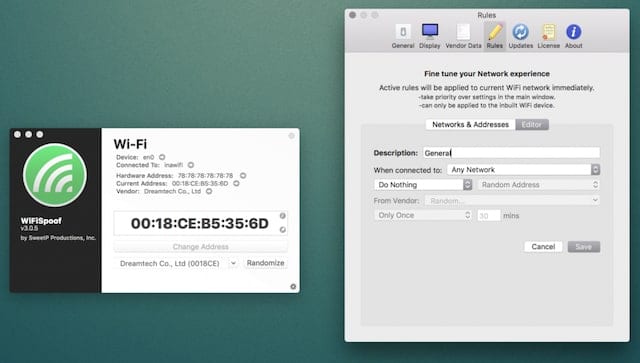
The app even provides a way to randomize a new MAC address every few minutes, a perfect way to prevent tracking while using a public network. It’s somewhat overpriced, but if you require complete security or do network security testing, the price tag for WiFiSpoof could be considered reasonable.













did not work on Mac Big Sur :)
how do i change it back to original
Well, IIRC, it’s not persistent (unless you do some stuff not mentioned in this article to assign the address every time upon boot), since you’re not changing it to be the PERMANENT MAC Address, you’re just spoofing it temporarily. So just reboot and you should be fine.
This did not work? I followed the directions exactly. In final step it says my MAC address is the same as when I started. I get this error – ifconfig: ioctl (SIOCAIFADDR): Invalid argument
I made a youtube video which explains this, would be cool if you featured it in the article!
Thanks for the contribution!
So I used this at home and it worked fine and all but when I got to school I could not connect to the school wifi could somebody explain what is causing this or how I can stop it but also keep my changed adresss?
Hi & thank you for free professional advise
unfortunately at stop 7 when terminal is
asking my password it doesn’t allow me to enter
anything apart of the enter return key nut than it
say as it follows….
ifconfig en1
en1: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
ether e0:f8:47:01:cd:ec
nd6 options=201<PERFORMNUD,DAD>
media: autoselect ()
status: inactive
Originals-MacBook-Pro:~ originalthesis$
openssl rand -hex 6 | sed ‘s/(..)/\1:/g; s/.$//’
1b:a7:fd:5f:43:12
Originals-MacBook-Pro:~ originalthesis$ sudo ifconfig en1 ether 1b:a7:fd:5f:43:12
Password:
Sorry, try again.
Password:
Sorry, try again.
Password:
you need to enter the password of your account when it prompts you to enter the password
that’s the thing though, when we type anything other than the enter key, nothing appears. what do we do?
When typing the password for sudo no symbols is shown, not even asterisks. You just type the password and press enter. The password stays invisible for security reasons.
Whenever I open Terminal after turning the internet off it wont work
hi i tried using this method to try to bypass my dads disney circe(firewall) but i still cant get through. is there any other way to bypass it?
i do the same to get past the disney circle and it worked for a bit but then it stopped changing. you can actually create a hotspot from an unblocked laptop without using any data and connect to that instead
When changing my MAC address there are multiple interfaces, displayed by the ifconfig command, which contain a MAC address. For ex. en0 en1 en2 en3 bridge0 p2p0 awdl0. I can change the MAC address for some of these however not all of them. Is it necessary/possible to change the MAC address for all these interfaces? And If not should I disable any of them when attempting to hide my address?
May 2nd, 2020
High sierra 10.13.6
I am proud to say that this is still working as of today.
Mine does not work i have a MacBook air 2014 with mac os Catalina. Does it still work??
February 7th 2020, using Catalina 10.15.3. Can confirm this is working ! as mentioned, keep the first 3 octets of the original MAC. EXAMPLE – XX:XX:XX:YY:YY:YY –> Keep the “X” of the original, change the “y”s
Cool.
mine still isnt working. i am confused!!
I can change built-in WiFi MAC address using ifconfig just fine.
I’ve never been able to change the MAC address of a USB WiFi adapter.
How does one do that?
I’m pretty sure that you would need to have a compatible usb wifi adapter. If you are sure about the usb wifi adapter being compatible, then changing the interface from en0 to the interface of the usb wifi adapter should do the trick.
Could VMWARE into Windows and then change the mac from windows if that’s an option.
i keep getting bad value when i try to spoof mac addy, it has worked in the past but today it won’t and is very frustrating i have tried and retried with no luck
I have reports that user with MacBook 2018 and later are not allowed to change (spoof) the MAC values. It seems Apple locked the value on these machines and nothing works to change them. Anyone with a 2018 MacBook can confirm?
Also Mac MACSpoof can do it at ecleti.com/osx/macmacspoof/
http://ecleti.com/osx/macmacspoof/
So this allows randomized MAC but what if you want to spoof with a computer that’s already registered to gain access to network privileges eg smtp ports etc?
Hello Phil your onto sometime here, how would I be able to exploit a system in this way?
For those saying that it does not work:
1. Keep the first 3 octets (XX:XX:XX:YY:YY:YY, keep the Xs)
2. Turn back on, the wifi before changing the MAC address
3. change address
Running on Mojave
Thanks. Finally someone who has a solution. It was working the way this website describes up until a couple days ago but now this seems to be working using your method.
Really appreciate the help, thank you whoever you are.
i dont get first step
When I entered the sudo thing and the new mac address, ifconfig: ioctl (SIOCAIFADDR): Network is down pops up. Can you help me?
False, this changes the IP on your terminal, but if you go to the network preferences you will see your Mac address is still the original one
Yes, the hardware is always the same, but in the software, you can trick the computer to connect using that MAC. So, yes, in network preferences you will se the same MAC address, however, you will connect using the spoofed address
I was able to change my MAC in High Sierra by ensuring the first three octets of the address stay the same as the hardware address.
XX:XX:XX:YY:YY:YY
Leave XX’s the same as hardware address, change YY’s.
Yup, this worked for me. Muchos gracias.
Really appreciate the help, thank you whoever you are.
How can you change it back to the original (hardware) MAC address?
MAC will restore when you restart the mac
Another reason to do this is to register a device that doesn’t have a web browser onto a network that uses a sign-in page – for instance to get an AppleTV onto a hotel WiFi. Get the AppleTV’s MAC address (it’s in the Settings menu), change (i.e. spoof) your laptop’s MAC address to the MAC address to the AppleTV, log onto the hotel’s WiFi with your laptop, and now your AppleTV can access the network without going through the sign-in page.
Do you only have to do this one time?
Is this a one time only thing – or will I have to do this every time I am at this location again? ie: using my mac at work, spoof using apple watch address, log on to work captive wifi, am I permanently connected? will this work?
I believe it is only permanent if you dont restart your laptop.
doesnt seem to work anymore. Im using MacOS Sierra 10.12.6. after ifconfig en0 ether , ifconfig en0 | grep ether still shows the old one :(
“Since we’re entering this command as root, we are prompted to enter the root password.”
This is totally incorrect. The whole point of the sudo command is to elevate a command to admin/root level so you don’t have to log in as root to do things. You would not enter the root password for sudo, you enter your own login password.
That is incorrect. Your own password is not sufficient. It must be an account with admin/root access. If yours is merely a user account, then your login account password will not work.
I should make an service app from automation app that you could just load with the startup items and sell it for $9.99. Think anyone would buy it, instead of paying $20?
why not just change it in network control panel?
How exactly would that be done? It doesn’t appear MAC can be changed by going to SysPrefs->Network->Advanced->Hardware
Once in advanced, go to the last tab which might say a few different things depending what you’re on. It’s in there on any fairly modern Mac. For older Macs, it might be elsewhere as it’s been a while.
Perhaps you can show us this in a screenshot, because we can’t find anything resembling a capabiity to change a MAC address in the Network panel.
I don’t seem to be able to send a screen shot.
go to advanced and last tab> Hardware
That doesn’t let you change the MAC address, just the MTU.
How different is this from using a VPN?
Quite different. This does nothing to change the IP address of the network connection you are using, which is what a privacy VPN masks by having you tunnel all your traffic so that it enters the open internet from their site.
Since you drop into terminal anyway, would a script like the following do the same thing? My only question about changing interface MAC is: does ARP have the current interface MAC cached in other devices on my network and if so, will the change confuse other devices about how to get back to my machine?
#!/bin/bash
IF=en0
export PATH=”$PATH:/sbin:/usr/bin”
mac=`ifconfig $IF | grep ether | awk ‘{print $2}’`
echo “$IF mac before change=$mac”
randmac=`openssl rand -hex 6 | sed ‘s/\(..\)/\1:/g; s/.$//’`
sudo ifconfig $IF ether $randmac
mac=`ifconfig $IF | grep ether | awk ‘{print $2}’`
echo “$IF mac after change=$mac”
My only concern with this is what if the randomly generated MAC address duplicates one that is already on the local network? That would be quite a mess.
The first six digits of a MAC address identify the hardware vendor. By generating a random MAC address, you are not just hiding who you are, but potentially presenting yourself as some other vendor’s hardware, which can have deleterious effects on some networks that actually care about such things.
To avoid this, you can make use of the convention that all hardware vendors are assigned MAC address prefixes whose second hex digit has a “2-bit” of 0. Any MAC address with a second digit of 2, 3, 6, 7, A, B, E, or F is guaranteed to belong to no vendor. Therefore it will collide only with other “random” MAC addresses you (or someone else) generated for yourself; and this collision can only occur within your local area network, as MAC addresses aren’t communicated beyond that (at least not in IPV4).