![]() Originally introduced with OS X El Capitan, System Integrity Protection, usually referred to as SIP, is a security feature built into the Mac operating system that’s designed to protect most system locations, system processes, and Kernel extensions from being written to, modified, or replaced.
Originally introduced with OS X El Capitan, System Integrity Protection, usually referred to as SIP, is a security feature built into the Mac operating system that’s designed to protect most system locations, system processes, and Kernel extensions from being written to, modified, or replaced.
SIP and related security protections in the Mac operating system have undergone changes with each release of the OS, but the basics of how the SIP system works have remained the same, including how SIP can be enabled, disabled, and have its current status checked on.
Rootless, More or Less
OS X El Capitan was the first version of the Mac operating system to incorporate SIP, as well as the idea that the Mac operating system was now rootless; that is, there was no longer a root account, the all-powerful primary account that had access to almost the entire system. But it turns out the concept of the Mac being rootless was more of a security marketing gimmick than actual fact. There was still a root account; the difference is that when enabled, SIP poses additional restrictions on the root account, walling off certain portions of the system from access by an account with root level privileges.
The additional isolation of system components from accounts with root privileges helps to prevent malware from being able to gain access to the system, where it could embed itself and take advantage of all of the system services running on a Mac.
System Integrity Protection (SIP)
While “rootless” was mostly marketing, SIP actually hardened the Mac by preventing modifications to the following locations:
- /System
- /usr
- /bin
- /sbin
- All apps preinstalled by Apple
The exceptions to the rule are apps or processes that have been signed by Apple and have a special entitlement to write to system files. This includes Apple installers and Apple software update services.
SIP is effective at stopping system locations from being written to by third-party apps and services. Only Apple-signed system processes can write to system locations.
System processes can’t be attached to. This prevents code injection or runtime attachment to system processes, techniques often used by malware to force privileged processes to run the malware code.
Kernel extensions must be signed with an Apple Developer ID that specifically allows for signed Kext (kernel extensions) certificates. This can prevent kernel extensions from being replaced or modified by malware, as well as prevent new unsigned kernel extensions from being installed.
SIP in macOS Mojave
Apple includes a number of new security-related upgrades in Mojave, but for SIP the big change is that it was extended to cover third-party apps and not just those supplied by Apple. This should protect third-party apps from being tampered with, having code injected, or having processes attached to them, all common techniques for gaining control of an app or its services.
Is SIP a Good Thing?
Without a doubt, SIP helps keep your Mac secure by preventing many malware attack vectors from being successfully performed. But like anything that brings restrictions to your Mac, there will be some fallout.
In the case of SIP, the most often cited problem is the failure of a legitimate app to install properly, or for an app to have some issues once installed.
For the most part, these app-specific issues were a problem when El Capitan rolled out and are far less of an issue now that developers have had time to work through the issues and create new ways for their apps to work with SIP restrictions.
The benefit for all users is that the Mac is a harder platform for malware to take over, though it is by no means an impossible task. Malware developers will always find new ways to attack a platform.
Controlling SIP
Although Apple would like you to always keep SIP turned on, it can be enabled and disabled as needed. In the early days of El Capitan, it wasn’t uncommon to disable SIP to allow a specific app to successfully install needed components in the various protected system folders. Once the install was complete, SIP could be turned back on to protect your Mac.
This SIP enable and disable dance has fallen by the wayside as developers found ways to work with the SIP system. However, if you have a specific need to disable, enable, or check the status of the SIP system, you can do so with these instructions.
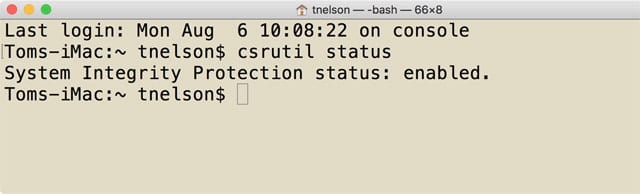
Check current SIP status:
Launch Terminal, located at /Applications/Utilities.
At the Terminal prompt, enter the following:
csrutil status
Press Enter or Return.
Terminal should respond with one of the following messages: “System Integrity Protection status: enabled” or “System Integrity Protection status: disabled.”
Enable or Disable SIP:
SIP can’t be enabled or disabled directly from within the currently running version of the Mac OS; instead, the Recovery volume is used to add a boot argument to your Mac’s NVRAM that controls the SIP system.
Because SIP is controlled through the Mac’s NVRAM, enabling or disabling SIP affects all versions of the Mac operating system you’ve installed. If you disable SIP to allow an app to be installed in OS X El Capitan, SIP will also be disabled if you should boot into macOS Mojave that you installed on another volume. SIP is a global setting that affects all systems installed on your Mac.
To enable or disable SIP, you’ll need to restart your Mac using the Recovery volume. Make sure you’ve closed all open apps, and then follow these instructions:
Restart your Mac. Once your Mac has finished shutting down, hold down the option key while your Mac starts up.
The Mac’s boot manager will appear, listing all of the bootable volumes you can start from.
Use the arrow keys to highlight the Recovery volume, then hit return or enter on your keyboard.
Your Mac will boot from the Recovery volume and display the Recovery Utility window.
Select Terminal from the Utilities menu.
The Terminal window will open.
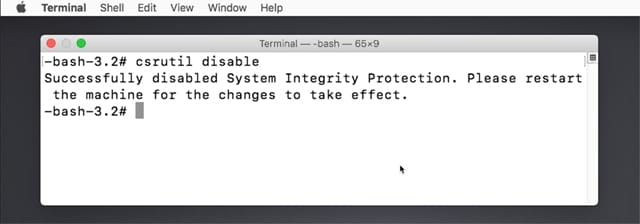
At the Terminal prompt, enter either:
csrutil disable
to turn SIP off, or:
csrutil enable
to turn SIP on.
After you enter one of the above commands, hit enter or return on the keyboard.
Terminal will respond by telling you it has either successfully disabled or enabled SIP.
For the changes to take effect, you must restart your Mac.
Close Terminal by selecting Quit Terminal from the Terminal menu.
From the Apple menu, select Restart.
Your Mac will restart with SIP set to be enabled or disabled, depending on which command you used.
SIP Best Practice
Most modern apps and their installers have become good SIP citizens, and won’t require you to disable SIP to perform an install. There are, of course, exceptions, especially with some popular Mac system and file utilities that require changes to be made in various system locations that SIP protects.
In order to install these types of apps, SIP will need to be disabled, the Mac restarted, the app installed, Sip enabled, and the Mac restarted.
You’ll find all the instructions you need to perform these tasks in this article, above. But before you proceed, ensure the following:
You really need the app in question. Is there a newer version or a similar app that doesn’t require alterations to the system, or disabling SIP to install?
If you must install an app that needs SIP disabled, make sure you’ve acquired the app from a safe source; direct from the developer is usually the preferred method. Remember that apps that require SIP to be disabled will be a target for malware distributors to use as a Trojan horse to hide within so they can infect your Mac while SIP is turned off.
Before you install an app that needs SIP to be disabled, make sure you have a current system backup or clone that could be used to restore from should the need arise.
After the app is installed, immediately enable SIP. Do this before using the newly installed app.
Enjoy your new app.
One last note: Future updates of the Mac operating system may restore system files and locations to the state expected by Apple, causing non-SIP-complaint apps to be marked as unsupported and possibly removed by a system update.
You may need to contact the app developer for a newer version to reinstall. Hopefully, they will have updated the app to work within the Mac’s new security frameworks.














I run Mojave and I also have VMFusion (windows) that won’t run without “csrutil disable”
If I try to run the program, I get “broken pipe etc…” Can’t there be a better way to run this?
When one has the firmware lock on, is there a way to boot up into Disk Utility? I’m finding this very difficult. I’d like to get into terminal or shut off the firmware lock. Thanks.
I disabled SIP as instructed and installed Catalina successfully on my mid 2010 white MacBook. It’s amazing,
It’s informing.
I just have installed a clean Catalina assited by Enterprise’s Branch at Apple with a senior mac advisor yesterday. This is a IMac 2017…I have done so because of a major cybersecurity issue dating from 2017 that has been prominent last October…so going on 13 months here….I have performed the terminal command csrutil status and it is disabled damn it. I have also noticed on speedguide.net that there is possible intrusion on port 443……I am desperately seeking help here…
Thanks for the info. I had to disable SIP in order to be able to restart Bonjour (turn off then on) which finally fixed my long standing problem with LAN printing. Interestingly, even after SIP being disabled, and being logged in as root, I could not remove apps like News or Stocks (but I could delete all package contents which does not make much sense to me).
Terrific article, as all are in your “Rocket Yard Weekly” newsletter. Please keep ’em coming!
Thanks, this was very informative as your newsletters always are.
I had to disable SIP in order to flash my (Early 2009) Mac Pro’s firmware from a 4,1 to a 5,1, so that I could install and run High Sierra, in order to use a new RX 580 Radeon video card for FCP X. Worked great, and made sure I turned SIP back on after! :) Thanks for the additional info OWC!
I really wish I’d known about this a long time ago. I installed Adobe Creative Suite 4 on both my 2010 iMac and 2012 MBP, running El Capitan at the time. Every time I launch Photoshop or Illustrator, I’d get a dialog box stating some components were missing and I’d need to reinstall the apps. They still ran, but with limited functionality, couldn’t add new brushes, filters, etc.
After disabling SIP, reinstalling CS4 is now working flawlessly, and I’ve been able to install a ton of new brushes, pallettes, filters, etc., and they work flawlessly! Even though I now run Sierra 10.12.6.
KUDOS!!! This was a god-send! Another confirmation as to why I’m fanatical about OWC!