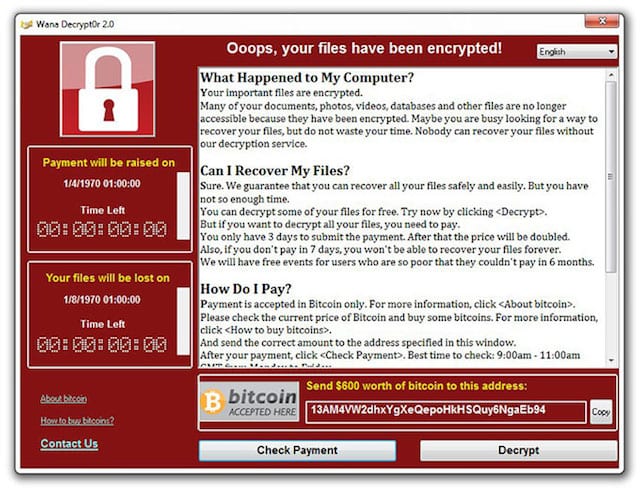
It was enough to make tens of thousands of PC users cry. A piece of ransomware named WannaCry infected those PCs, encrypted all of the files, and then demanded a ransom payment before the encryption could be removed. This was the case last week around the world as those thousands of PCs in homes, businesses and government offices were rendered useless. While WannaCry didn’t hit Macs, the next piece of ransomware could. Today, we’ll talk about how to protect yourself against ransomware.
Make Sure You’re Running The Latest Version of macOS
WannaCry targeted the computers that were the most vulnerable to a malware attack. In this particular instance, the computers were all running Windows XP, an operating system that originally came out in October of 2001. While most of the PCs had probably been updated to at least Service Pack 3, that still happened in April of 2008 — a full nine years ago. Windows XP is still widely used in automated teller machines (about 95% of all ATMs worldwide run XP) and medical devices, both systems that are rarely updated. As a result of WannaCry, Microsoft actually issued a patch to the operating system on May 13 for these custom devices — all for an operating system that is in “extended support” and hasn’t been sold for nine years.

What’s the moral of the WannaCry story? Make sure that you are running the latest version of the operating system on any of your devices. Sure, you may want to hold onto that iBook running Mac OS X “Leopard”, but if you do, either run malware detection and deletion software on it or do not let it access the internet. If you must use that old machine running a legacy operating system to access websites, avoid downloading attachments and don’t click on links in emails from unknown senders.
Do A Regular Full System Backup of Your System
At the risk of sounding like a broken record, the team at the Rocket Yard wants you to do regular backups of your computers. With ransomware, a full backup makes recovering from an infection much easier and potentially less expensive than paying a ransom. Instead, what’ll you’ll do is start your Mac in recovery mode (hold down the Command and R keys on the keyboard during boot up), erase the ransomware-encrypted internal drive, install a new copy of your Mac operating system, and then restore the system from your backup.

With macOS, getting those backups done can be as easy as purchasing an inexpensive external hard drive from MacSales.com. Whether it’s a 2TB USB 3.0 OWC Mercury On-The-Go Portable Drive that you connect to your MacBook Air, an OWC miniStack for your Mac mini server, or a massive OWC ThunderBay 4 RAID 5 array for a Mac Pro, MacSales.com has a solution that is perfect for you.
With the smaller drives, it’s possible to use Apple’s own Time Machine backup software that is built into macOS to perform the backups; in fact, connecting a drive to your Mac results in the operating system asking if you wish to use that drive to perform backups with Time Machine. For bootable backups, a third-party software solution like Carbon Copy Cloner, Backup Pro, SuperDuper!, or Prosoft Data Backup can make getting back to work after a ransomware infection as easy as just rebooting, holding down the Option key on the keyboard, and selecting the backup disk to boot from (you can erase and reload the primary drive later).

Unplug That Backup Drive
Now this is something new. Experts are suggesting that once a backup is completed, you unmount it from your Mac and unplug the cable. Why? Some ransomware has been designed to infect data on connected drives as well as the boot drive, so keeping a drive attached 24/7 could result in an infected backup drive.
What’s the solution? Perhaps consider having two external backup drives. One can be connected at all times for incremental backups like those performed by Time Machine, while the other can be plugged in once daily for a quick update.
Install and Run Anti-malware Software
In the past, I’ve personally recommended not installing antivirus or anti-malware applications on Macs because of the low incidence rate of viruses and other malware. With the rising popularity of Macs, malware is an ever-present danger to the platform and for the past several months I have been running ClamXav ($29.95) on my iMac.
There are many other solutions, of course. Malwarebytes is free for home use, BitDefender Antivirus for Mac runs $45, ESET Antivirus runs between $39.99 and $59.99 depending on the level of protection, and there are a number of other apps available. I chose ClamXav because it doesn’t slow down my Mac, it’s continually updated with new virus definitions, and it’s unobtrusive.
Keep these simple ideas in mind when using your Mac and perhaps you’ll never find yourself reaching for your wallet to pay a ransomware demand. Any ideas you would like to contribute for staying safe in the age of ransomware are greatly appreciated; just leave them in the comments section below.










Can you run ClamXav and Norton Utilities at the same time?
Good article. For bootable backup, I set SuperDuper to run automatically when my backup drive is mounted. I leave it plugged in and turned off. Once a week, I turn it on, let SD do its magic, and turn it back off again. I also have Time Machine and CrashPlan for any file created since the last bootable backup. I’ve experienced hardware failure and user error, but never lost more than a few hours of work using this triple backup system.
I am running the current Mac OS and have multiple mackups and Avast anitvirus installed. However, have Parallels installed along with both an early version of Windows XP and an early version of Windows 10. I almost never launch these virtual machines (maybe once every two years). Any idea if they make me vulnerable to ransomware?
What if your computer is no longer supported & cannot run the latest OS? For example mine is early 2008 and cannot go beyond El Capitan.
Worth mentioning: Don’t log into your Mac as an Administrator. When a program asks permission to install, you get a chance to think about it!
I’ve a set of four drives in an enclosure that’s connected but only turned on when making a backup. Is the enclosure still vulnerable if it’s powered off?
If the enclosure has a physical on/off button, and it’s off, no power goes to the drives, so nothing can be written on them.
If it has a “soft” power button (and it can be commanded by software), there’s a slight possibility that a malware could switch it on and write on it. But that’s quite unlikely.
If you’re unsure, you can connect the enclosure to a power strip with a switch, so you can be sure that it’s off for good.
Good, the enclosure is physically off – no power to any drives so there’s no r.w activity.
I also have clamX running so it seems I’ve a reasonable chance of avoiding catastrophe
Sophos Home for Mac is free. It’s the AV software our company uses for Windows & Mac. It has nice features for free. (Can see all your Machines on one account) for example.
And keep antivirus background activity off to avoid interference with Mac. Manually check files.
Hi Steve,
Excellent article, as usual, but I wish you could also cover the OnLine backup services like CrashPlan, BackBlaze and others.
It’s my understanding that they will only provide a pristine backup if the service keeps staged or versioned copies of yesterday’s backup and earlier.
This is vital information for those of us that rely on such a service for their Off-Site backup.
Crashplan specifically states it is intended for data only, not a complete system backup.
The best plan for restoring a Mac is to keep a full backup locally.