It’s hard enough protecting yourself, but too many big corporations out there put you at risk.
There is not a lot you can do about it other than looking elsewhere, which is often impractical. This article discusses some of the most common Worst Practices and offers some ways to minimize the risks.
See also: Computer Security: 7 Rules to Keep Hackers at Bay
Corporate Security Worst Practice #0: The really dumb stuff
Believe it or not, many companies out there are still doing really dumb stuff with security. Hopefully, no company still stores cleartext passwords, but some probably do. Some store hashed passwords—passwords that are run through a hashing algorithm to convert the password text itself into letters and numbers—but fail to ‘salt’ them, making a brute force password cracker’s job easy. That’s the really dumb stuff.
Recommendation: every web site should have a different password. Never use the same password in more than one place.
Then we have the unencrypted security questions/answers. These are almost equivalent to cleartext passwords, and yet in December 2023, a major internet provider recently compromised 36 million accounts this way.
“…the customer information in scope included usernames and hashed passwords; for some customers, other information may also have been included, such as names, contact information, last four digits of social security numbers, dates of birth and/or secret questions and answers. However, the data analysis is continuing.”
Corporate Security Worst Practice #1: Forbidding good passwords
I once spent hours puzzling out why when I changed my password, I could not login… it turned out that the web site disallowed more than 12 characters. The site would let me enter, say, 24 characters, then silently truncate it to 12, and then I had to do reset password all over again. After about 10 tries, I finally figured out the problem.
Web sites all too often require arbitrarily short passwords, along with restrictions on which characters are allowed. The reason is engineering incompetence, because all passwords should ultimately be hashed (with “salt”) to the same length (the “hashed password”). Not only do such sites require reduced security, it forces you to break any personal password system methodology that you might have, being forced to dumb-it-down to exceptions, which in turn forces reduced security by writing down what you now cannot remember.
Recommendation: use a password manager so that you can supply a random-gibberish password that you do not have to remember.
Corporate Security Worst Practice #2: Forced password changes
This is one of the most egregious bad practices and actively degrades security by using social engineering the wrong way: harassing people to constantly think up new passwords. The government does this, as well as many HR departments and the services they contract with.
It relies on the false assumption that somehow passwords “go bad” or will be compromised over time. There is some truth to that, but not much. It actively penalizes those who follow good password hygiene.
I find it impossible to remember my passwords when I am forced to change them every 3, 6, 12 months or whatever the policy demands. You?
Forced to constantly create new passwords, you take action: you simplify. You write it down. Or you start reusing the same password (or minor variations) on multiple sites because constantly coming up with new passwords that you can remember is hard. It becomes a hassle, a security management chore, like filing your taxes every year. Just having to do it almost certainly leads to shorter lower-quality passwords—why would you make the effort for a better one?
Recommendation: use a password manager so that you can supply a random-gibberish password.
Corporate Security Worst Practice #3: Good, strong passphrases are troublesome
Negative feedback loop: the better your passphrase, the more you dislike it.
Asked too often for a strong password, you have little choice but to simplify, then simplify some more. This “ask more often” approach—that Apple is increasingly fond of using—adds a strong incentive to keep it short and simple, which means less secure. Not good.
But maybe you choose a good strong passphrase anyway. Not only does it take more care to type it correctly, you must do so while BLINDED to what you are typing: the box shows only bullets. After 2 or 3 failed attempts due to a typo, the device threatens to lock you out of your account. This is now not just annoying, but stressful. And because you cannot see the error, you have to erase it all and start from scratch each time, keeping the odds high of yet another typo. I cannot think of a worse possible design—and yet that is exactly what Apple does.
Apple de facto encourages low-quality passwords, because a strong one is a hassle.
For example, I use a strong passphrase for iCloud and Apple Store. To buy an app, I have to enter a complex passphrase, which I get wrong at least 2 times out of 3, because I can’t tell if I’ve made a typo. I frequently just give up. This is precisely what Apple foists on its users, and why I loathe using my iPhone or iPad for anything but email and web sites.
System design is destiny: people switch to a short and sweet password, the worst possible outcome. But instead of fixing a key problem, Apple piles on biometrics, which carry their own issues.
Recommendation: use a password manager to reduce the hassle factor.
Passkeys are the claimed fix for all this mess. But even I, a software engineer, find passkeys puzzling. They seem too magical to feel safe, and are unavailable across all my devices and services (never for some of my older Macs). Nor am I a fan of biometrics. Support for passkeys is growing, but it is still very much a random here-and-there thing. And how would I explain passkeys to my father when it requires understanding and setup I have found to be troublesome? Passkeys were invented by nerds, for nerds.
Corporate Security Worst Practice #4: Canned security questions
We’ve all seen it: fill in these security questions to make sure we can verify it’s you.
Except that the questions are usually fixed/unchangeable, and so the answers are always the same. For all websites. Which many people dutifully fill-in, the same answer everywhere, every time. That’s the worst possible security. And it’s commonplace.
Along comes a security breach (not your fault!) and the answers to those canned questions, likely to be immutable personal facts, are now exposed forever to the world. Forevermore insecure and thus dangerous. QUICK! Try to remember every web site where password-reset security questions are used, login now, and change the answers.
“…the customer information in scope included usernames and hashed passwords; for some customers, other information may also have been included, such as names, contact information, last four digits of social security numbers, dates of birth and/or secret questions and answers. However, the data analysis is continuing.”
Here in 2023, wholesale incompetence meaning a failure to follow Best Practices, instead storing all this information in the clear (unencrypted). OMG.
Recommendation: answer those security questions with a unique gobbledygook answer on each and every web site that uses them. You’ll then need to security record those answers somewhere thus creating a new security risk.
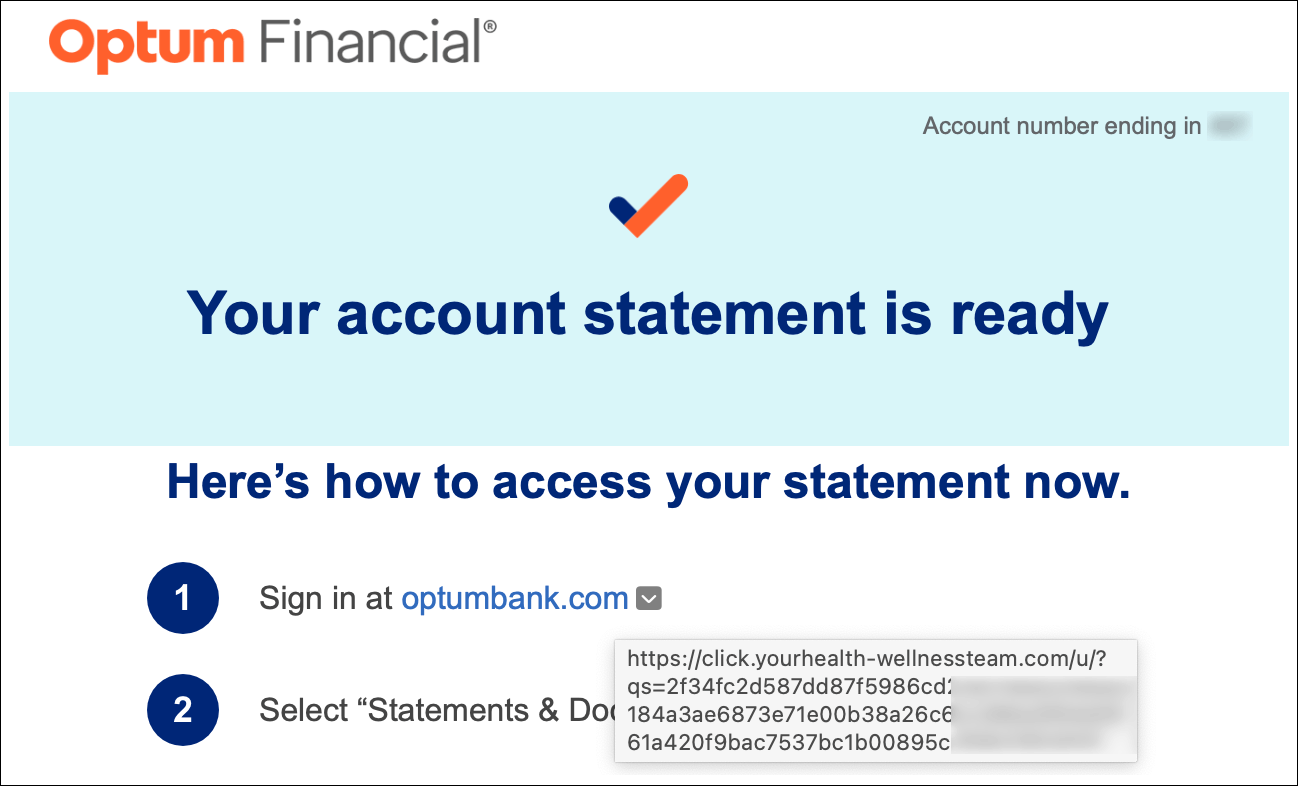
Corporate Security Worst Practice #5: “Helpful” emails
Are you kidding me? How can I tell this link apart from some phishing scam? A long inscrutable link does not inspire confidence (if you even see it the actual URL as shown here).
Recommendation: assume that links in emails are phishing/fraud. Look up phone numbers and go to web sites manually.
Conclusions
There is minimal incentive to protect your information, there being no meaningful liability. All the costs of a security breach fall on you. What can you do? Assume whatever information is out there will be compromised.
It starts with accepting reality: you cannot fix bad practices on the other side. All you can do is minimize the damage they will cause you—it’s a matter of when, not ‘if’.
See also: Computer Security: 7 Rules to Keep Hackers at Bay
UPDATE: in an ironic twist, as I was putting the finishing articles on this article, I opened a letter from my mortgage servicer. It stated that all my personal information had been compromised, including social security number. Their “solution”: two years of “free” credit monitoring plus endless hours of MY time spent to monitor this stuff over the coming years. My reaction is unprintable. What I want—and will not get—is total indemnification for the next 10 years, along with personal liability for executives, so that corporations and their highly-paid leaders pay a heavy price for their security sloppiness. What could I have done? Perhaps nothing. These mortgage companies require your information, and keep it to defend their loan should any issue come up. But IMO, the law ought to require destroying all of it within, say six months.
View all posts by Lloyd Chambers… Lloyd’s photo web site is diglloyd.com, computers is MacPerformanceGuide.com, cycling and health at WindInMyFace.com, software tools including disk testing and data integrity validation at diglloydTools.com. Patreon page. Lloyd also offers consulting on camera systems and lenses, professional setups for photography/videography and backup.









A response to this post of how an older reader deals with security is found here: https://macperformanceguide.com/blog/2024/20240130_1300-OWCBlog-HowCorporateSecuritySloppinessPutsYouAtRisk.html
It may have some quit useful tips.
Thanks, Lloyd,
A very useful article. I might add one gripe that I have yet to resolve. I use Safari on both my iMac and my laptop. I find that often, when I randomize a password, via Safari, on the iMac instead of using a formulaic version, Safari’s password manager doesn’t communicate the change to my PowerBook. I often have to go through the password game when I’m on the road for that reason. Gee, maybe I should carry the printout with all my usernames and passwords with me on trips?!
I too have found that syncing between devices can be slow or delayed or sometimes just not happen—really frustrating.
OTOH, I have found that 1Password syncs-up very quickly. I do not use Safari’s password manager; it’s far too limited for my needs.
I also use 1Password but, for some reason, the 1PW logon for my laptop is different, and much longer, than the one on my iMac. I’m not sure they’re synchronizing. So I fall back to Safari’s.
Sounds to me almost like you have two different 1Password setups—not sure.