This post builds on my previous post: How Corporate Security Sloppiness Threatens Your Online Life and How You Can Reduce Your Risk.
A fact of life is that security is extremely hard—not for technical reasons, but for people reasons.
When I was working as an engineering manager in the computer security field, the top issue was never the security itself, but how to make things as secure as possible while keeping things usable. Endless discussions lasting hours. Security is as weak as its weakest link, and today that is almost always the people involved.
Thus any approach that is “best” is ludicrous when people cannot use it and/or understand it and/or make mistakes with it. People start doing seriously risky things when security is too hard to use. Security always involves some kind of tradeoff vs. complexity.
Risk management
Bad to terrible outcomes: too many people have been subject to security hacks that have cost them dearly, with problems that take years to clean up. Some breaches are irreversible (eg. financial loss), some are longterm headaches (e.g. ruined credit rating), some are embarrassing (e.g. blackmail), some are life threatening (e.g. false arrest due to stolen identity). Don’t join this unlucky club!
Risk management starts with understanding the simplest things you can do to protect yourself with your own best practices. Just as with walking down a city street, it’s on you to have situational awareness. Even big companies with strict policies have problems with security, which means individuals absolutely have them as well.
After all, it’s a mine field out there. Legislative uselessness driven by corporate disinterest is to blame for much of the danger because their priorities are not your security. This dangerous ground is not likely to change any time soon, in spite of lip service given to it. There are of course islands of good practices here and there, but the total environment remains risky. And security rests on the weakest link.
And not just from hackers, but also from the reckless practices even today of many big companies, who have little to lose when security breaches happen. You will not be compensated for their mistakes. You may be blameless, but you will pay the price, not that company whose failings led to it.
Can’t a password manager just fix it all?
Password managers are all the rage and for good reason, but they are no panacea. And IMO, among other problems, they have become overburdened with complexity and frequently fail to work with some web sites. The overall recommendation is solid, but it is the most glib and context-free recommendation you’ll hear today. Yes, use one, but not everyone can grok one, and it is not without risk itself.
For example, my own father finds a password manager too complicated/confusing, and that is not going to improve as he ages. Can you teach grandma how to use one?
Here in 2024, my favorite password manager has become such a hassle to setup on a new computer that I have to revisit the directions and jump through multiple hoops and compromise a required secret code (eg. store it on my computer) for fear of losing everything. A terrible design for a password manager. All because that vendor forced a move to cloud-only and their new architecture prioritizes their needs, not mine.
Before, it was far simpler and without that secret key risk—far better for me. Just not for the vendor. That vendor will surely argue otherwise, but as a software engineer writing code for 40 years, I beg to differ.
So, where does this all leave a non-engineer when it comes to protecting themselves?
Rules
Let’s look at the basics of protecting yourself. This is not a complete list, but it is a start down the right path. And to my regret, it’s not all that simple. Alas, that is digital life today.
Security Rule #0: Trust is the opposite of security
All the other rules that follow become useless if you willingly give up sensitive information. Whether it is by phone call or text or email or in person, giving up sensitive information is your ticket to disaster. Always independently verify the identity of every request for information, and provide as little information as possible.
- Do not assume a phone call is legitimate. Look up the phone number yourself, and call back. I have been called by myself according to caller ID!
- Never click on links in email. Never.
- Voices can be faked to near perfection—the caller might be an AI voice.
- Never “help someone out” with security information.
- Even simple things like where you live, birthday, etc. can be used to get into one of your accounts.
- The list is endless.
All such social engineering practices rely on social norms. Learn to resist the pressure and violate (appropriately) social norms of courtesy and trust in all security situations.
Security Rule #1: Never use the same password more than once
Rating: essential
So convenient isn’t it? Same password for your iPhone, iPad, Mac, and maybe some online sites. You might as well walk around with a T-shirt reading “easy mark, steal my stuff please”.
When a hacker obtains a password, that hacker now can access all of the accounts that share the password. And possibly reset other accounts via password-reset mechanisms, using the compromised accounts as leverage (e.g. one account such as mail can be used to confirm a reset for another). Or guess other similar passwords… a snowballing effect. All automated and essentially instantaneous.
- Using the same password for your Mac as for iCloud or your phone is a terrible practice.
- Your email password should be especially high security, since email is usually the key to compromising all your other stuff (e.g. password reset). Therefore, your email password should never be shared for anything else, or be in any way similar.
- Do not use passwords that vary only in minor ways. Hackers will quickly try variants and additions.
Security Rule #2: Use a Strong PassPHRASE
Rating: essential, but in limited contexts
Due to the hassle and errors in entering a long sequence, this rule is really only practical for unlocking really important stuff e.g. unlocking the vault of a password manager.
The more important something is, the stronger the passphrase should be.
Random-character gobbledygook passphrases at least 16 characters long are best, but using them de facto requires a password manager, barring some perfect memory and perfect typing skills. Therefore…
Think passphrase, not password—as in multiple words. If you’re me, you can probably remember “My Cat Tigger Loves Rats and Gophers 24×7”. It’s never going to be hacked/guessed, and now I can never use it. Substitute a few numbers and punctuation instead of letters (invent your own personal rules), and you’re golden.
Summarizing, this is a classic “usable vs. secure” tradeoff: it’s inconvenient and error-prone to enter a high-quality passphrase, so you choose a short and easy one. Use it when feasible. Indeed, Apple makes this much worse by making it nearly impossible to enter correctly because what has been typed is hidden from you with bullet chars—your typos are hidden from you (yes, this happens to me a LOT). It is why I loathe entering my iCloud or App Store password—pretty soon I am getting the “too many errors you are about to be locked-out” thing.
Security Rule #3: Learn to use a password manager
Rating: strongly advised, but might be too hard for some.
That spreadsheet or text file or scrap of paper on your desk with all your passwords on your computer is a massive risk. Yeah, I ‘get’ that you need some means of remembering them all, but think about what it means if someone gets to it. That includes in your backups, everywhere they are. For such an approach, at least get things onto an encrypted thumb drive that can be removed and locked up. And make sure that every backup containing that sensitive stuff is encrypted.
I use a password manager, and could not work efficiently without one. A password manager is a huge time-saver and comes with some less than obvious benefits, plus some risks:
- Once unlocked, a password manager can not only fill in logins (with varying success), it can fill in name/address/credit card/etc. This saves a ton of time.
- You no longer have to remember your passwords, so that they can be long and messy and different for every login.
- Securely store notes, special information, etc.
- I don’t even know most of my passphrases now. Which means deniability e.g. if someone wants to force you to reveal a particular password (think border crossings, thieves, etc.) On the flip side, if your PM password is compromised, the entire vault is open for everything inside it.
- RISK: if you compromise your vault password, all your passwords are compromised. See Rule #2 on strong passphrases and what happens on phone, tablet, computer.
A password manager eliminates the keep-it-short + enter-into-spreadsheet doom loop. However, a password manager is an “all eggs in one basket” approach, and so the passphrase for this “vault” must be strong and never compromised. And you must consider its risks on phone and tablet and computer. For such reasons, I use it only on my computer—I just do not want to deal with it on iOS.
With a password manager, have an outstanding high-quality password for unlocking it, and be extraordinarily careful about where you type that in. That one master password unlocks your world. And that is the only serious downside of a password manager, assuming it is engineered properly. Nothing is without risk, but a password manager is vastly superior to a text file or spreadsheet. Finally, consider what happens when you die and make sure that your heirs know the password manager passphrase.
Password managers have been breached before. The only one I am prepared to recommend is 1Password because they appear to do everything “right” from a security perspective, and I say that based on years of engineering experience with encryption. Which is not to say I like the increasing complexity of a do-it-all app—the earlier versions were easier for me to understand and manage.
Security Rule #4: Require a 2nd confirmation for login (2FA)
Rating: essential for anything important
2FA means “2 factor authentication”. One factor is your traditional login e.g. name + password. The other factor is something else, such as a one-time code sent to your device, or biometrics, or a separate device.
2FA greatly enhances security because all items must be compromised. And there are ways to defeat this, such as phone-number porting (convincing the phone company to switch your phone number to another phone), so it’s not perfect.
Many if not most web sites now allow pairing a login requirement along with a one-time code to complete the login. Some allow bypassing this for your computer (check a box to skip), which might be reasonable when at home. Or might not—consider people who have access to your home..
Phone/tablet-based one-time access codes are the simplest and best form of 2FA. Very high value vs. not having it.
However, there are schemes to compromise phones (steal your number). These are outside our scope here, but make sure such accounts themselves are as locked down as the provider allows.
The best 2FA involves the use of a hardware device you can keep with you, such as on your keyring. These emit a new code every minute or so. Sadly, the number of sites supporting such devices is so few and so different that in practice they are a non-solution. That said, if your bank or brokerage or similar offers them, that is your very best choice.
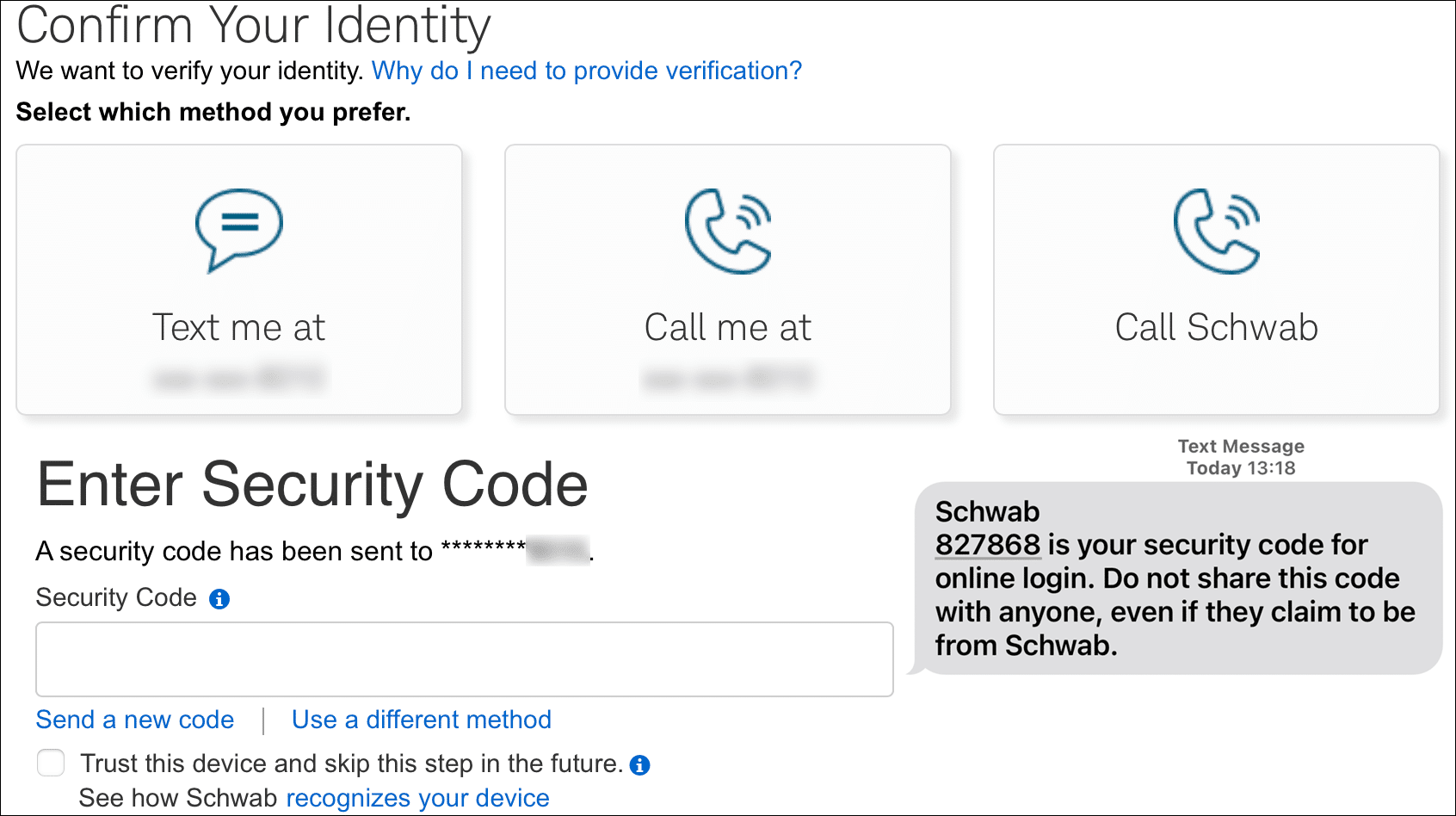
Security Rule #5: Never click on links in emails
Rating: strongly recommended (bad habits become automatic)
Phishing links in emails are a top way to breach security. This is why companies train and/or forbid employees from clicking on such links or even remove them entirely. Unless you are certain that an email is legitimate (are you an expert?), never click on a link in an email. And definitely NOT from your friends or associates—think fake or unwitting emails. Not “check this out” emails. Not from Apple, not from the IRS, not from your family—what if their email had been compromised?
Not from anyone. That is the only safe way to operate. You may make exceptions as I do, but only in specific circumstances. The problem is that once you break a rule/habit, you WILL break it that one time when you should not have.
Unfortunately, many companies persist in sending emails with messages that essentially look like phishing emails: “click here to do this useful thing”. How can you possibly know if these are legitimate? I can do so 99.9% of the time, but what about you, and what about the average computer user?
The first group of hackers that makes phishing emails look 100% legitimate (easy to do) is going to have a much higher hit rate. Usually there are obvious errors.
Currently, most phishing scams like the one shown below are obviously fake when examined. But at a glance, many a person is fooled, making it a profitable scheme. And a glance is all most people do, most of the time. For that reason, never ever click on links from anything that looks like it is from a financially related company.

Security Rule #6: No promiscuous web browsing
First, never visit insecure sites (plain http not https); your browser should warn you when visiting a non-secure site, albeit maybe poorly. Strikingly, there are still a lot of legitimate web sites out there that have such poor security that they either have no https (encrypted form) or allow either http or https connections. Such sites should be strictly avoided, used only in the greatest need, since such reckless configuration also suggests web site compromise as a strong possibility.
“Promiscuous web browsing”. There are several forms of this, and my wife does them all, which drives me crazy, though I am slowly training her as to the dangers. So many juicy enticing salacious links to click on!
Sooner or later, one of these will lead you to a compromised website with malware. Or less toxic but still a scam, it tmay take over your computer screen with a scary warning about how it is infected and to click here to pay and get it fixed. In which case you get some nasty crapware that if it is not outright malware will crash your machine or demand an upgrade or some such. This happened to a relative of mine, an otherwise highly intelligent person.
Similarly, any click-bait web site can rapidly lead you to dark corners. You might like that salacious “news” site, but you will end up paying the price.
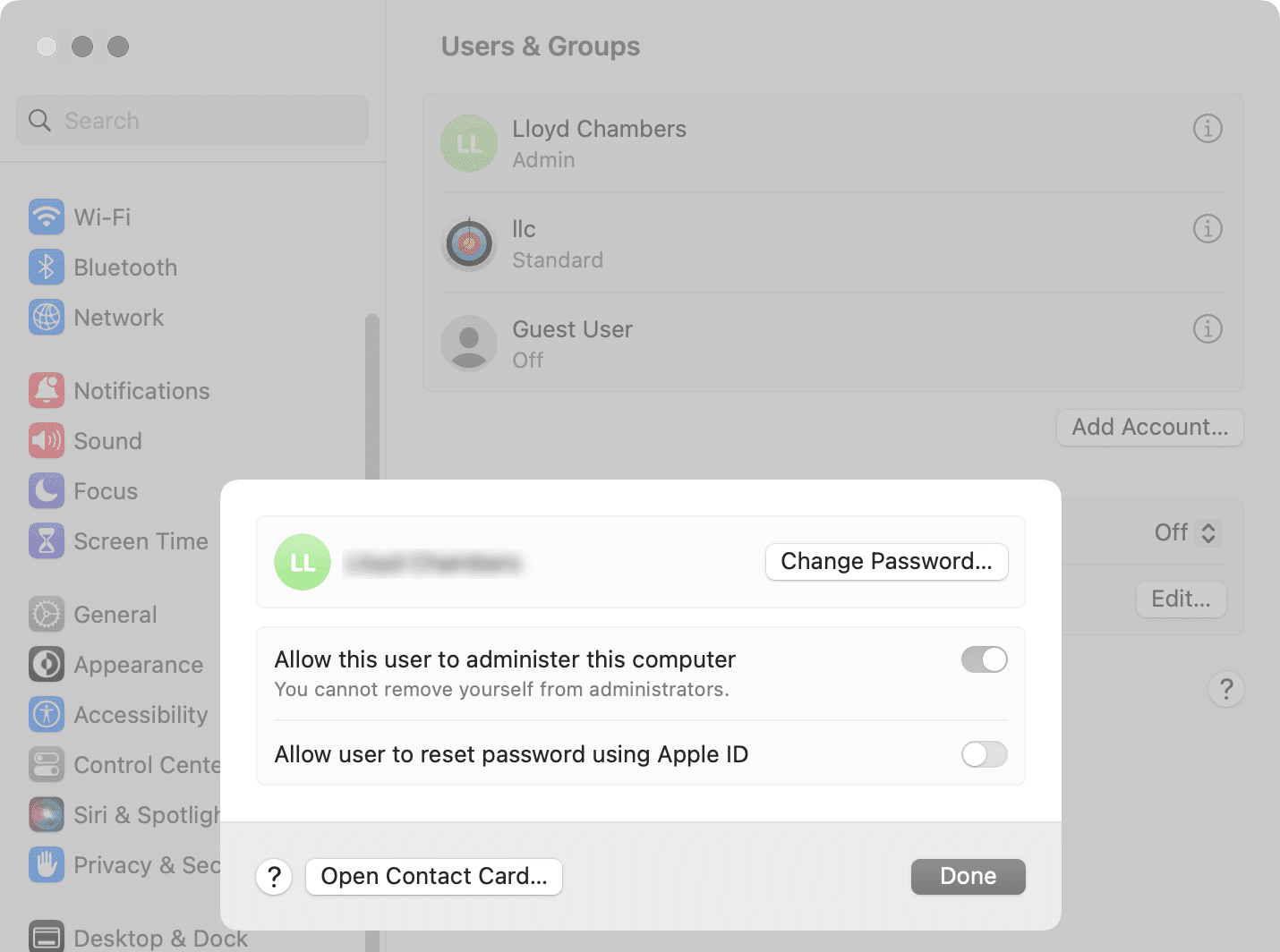
Security Rule #7: Non-administrator login on your Mac
This might or might not protect you, since Apple itself has had so many “zero day” problems in the past few years. But you can only do what you can do.
Consider adding a non-administrator account in System Settings => Users and Groups. You will have to add another account, and unfortunately Apple does not make it simple to move your stuff between accounts. For this reason, it is best done when setting up a new Mac.
Conclusions
Certain improvements in security can be had with relatively little effort. You cannot control for bad practices or security bugs, but by following at least some of these rules, you can greatly reduce the risks that you can control. Proceed in stages, with the easiest things first, and go from there.
Did I keep things reasonably simple? Not to my satisfaction. Security is a very hard nut to crack, and simplified advice usually ends up being simplistic. Still, I hope that by touching on each of these areas, a broader viewpoint may help you may smarter choices.
This article was an overview, not a how-to. Please leave a comment as to which item(s) would be helpful as to how to do certain things.
Author’s background: besides a degree in mathematics and computational science, and six different startup companies and Staff Engineer at Sun Microsystems and Oracle, Lloyd worked in the security (encryption) industry for several years as both an engineer and engineering manager, namely at Pretty Good Privacy (PGP). Lloyd was also responsible for application server security at NetDynamics, later acquired by Sun Microsystems.
View all posts by Lloyd Chambers… Lloyd’s photo web site is diglloyd.com, computers is MacPerformanceGuide.com, cycling and health at WindInMyFace.com, software tools including disk testing and data integrity validation at diglloydTools.com. Patreon page. Lloyd also offers consulting on camera systems and lenses, professional setups for photography/videography and backup.