On March 4, 2016, Palo Alto Networks sent out a warning about a new piece of ransomware that affected Mac OS X. The ransomware was named KeRanger, was infecting installers for the popular open source BitTorrent app Transmission, and as you’d expect with something called “ransomware”, it encrypted the users’s data and then demanded payment in the form of one bitcoin (about $400). Should you be worried about KeRanger? No, since it’s already been shut down by Apple, but you should take care to prevent a similar future piece of malware from ruining your day.
Normally, your Mac protects you from possible malware through File Quarantine. This piece of security software is what warns you that you’re about to launch an application that you downloaded from the Internet. Most of the time, you are aware that you’ve downloaded an app from the Internet, and you’re also quite willing to install it.
Next, if File Quarantine sees that the app you’re launching is included in the XProtect malware definitions, you get another warning — much more severe in tone — that tells you what malware is about to attack. Well, KeRanger had been signed with a valid Mac app development certificate, so it was able to easily bypass the usual Mac Gatekeeper protection mechanism. Those who were unlucky enough to have downloaded the infected Transmission app installer between 11 a.m. PST on March 4 and 7 p.m. PST on March 5 got to sit by helplessly while their data was encrypted and they were told to “send money” to get it unlocked.
Fortunately, Apple has revoked the developer certificate and also added KeRanger to its malware definitions list over the weekend, so your Mac is currently pretty safe from this nasty piece of work. Those malware definitions are auto-uploading on your Mac, and XProtect has been part of OS X since version 10.6 Snow Leopard. By the time most people even heard about KeRanger, they were already protected from it.
Let’s think about how those affected by KeRanger could have responded instead of paying ransom, and how you can stay away from future ransomware. For those who were affected by KeRanger, the best thing they could have done was to immediately shut down their Mac, install a new clean copy of OS X from the Recovery Partition or from an install flash drive, and then recover their data from Time Machine or another backup.
Palo Alto Networks notes that the attackers might be trying to figure out a way to encrypt users’ Time Machine backups as well, which would make it even harder to recover from a future version of KeRanger. So how could you stay safe from ransomware like this?
There’s a relatively easy way to make sure that your backup would be safe from ransomware, and that’s to make a daily bootable backup with Carbon Copy Cloner or SuperDuper!, and then unplug the drive you’ve made the backup onto. Should ransomware infect your Mac and your constantly-running Time Machine backup, you’d still have a clean backup that you could use to get back to business quickly.
Is there any way you can totally protect yourself from malware like KeRanger? Yes, if you only install apps from the Mac App Store where they’ve been vetted and checked for malware prior to their release to the public. Sadly, a growing number of disgruntled app developers are moving their apps from the Mac App Store to their own online web stores, citing the inability to offer free trials of software in the App Store and slow approval of new or updated apps.
As it is, if you did download the Transmission installer recently and haven’t launched it yet, you probably want to download a new copy of the installer. If you happened to get the bad copy a second time, a message similar to the one seen below will appear on your Mac:
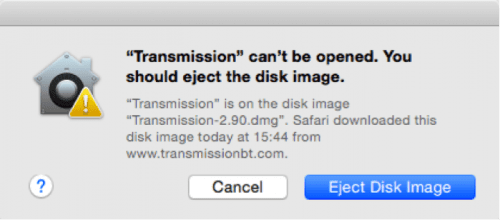
This should be your clue to delete the installer immediately. Palo Alto Networks also provided some good instructions on its website regarding specific files that should be removed and processes that should be force quit in case of an infection with KeRanger.
Keep your backups up to date, watch out for suspicious app installers, and be sure to have a backup drive that’s not connected to your Mac. We at the Rocket Yard want you to be safe!














Unplugging disks is problematic. Especially if they are Daisy Chained. Do you have a solution for this? A switch or gate of some kind? A way to manage thick stiff and lengthy cables? Manage big heavy and clumsy boxes like Raid enclosures?
http://www.bresink.com/Images/NAS200.png
“Is there any way you can totally protect yourself from malware like KeRanger? Yes, if you only install apps from the Mac App Store”.
Sometimes that is not possible. For instance, in the case of TinkerTool System, which is not allowed by Apple:
Full software, not an App!
http://www.bresink.com/osx/FullSoftware.html
http://www.bresink.com/osx/TinkerToolSys4.html