
Last week, the Federal Bureau of Investigation (FBI) released a statement saying that all consumers and small businesses should reboot their Wi-Fi routers and NAS devices. If you haven’t yet taken the time to do this, check the rest of this post to see why following this simple security action is necessary and then go do it.
VPNFilter Malware
The FBI’s statement came out after Cisco’s security researchers discovered that more than 500,000 Wi-Fi routers were infected with malware named VPNFilter. According to Cisco, Linksys, Mikrotik, Netgear, QNAP and TP-Link routers are all affected. Further research by the U.S. Department of Justice (DOJ) showed that the malware was crafted by the Sofacy group, linked to the Russian government, and that Ukraine was the intended target of the attack.
Cisco reported that “The VPNFilter malware is a multistage, modular platform with versatile capabilities to support both intelligence collection and destructive cyberattack operations.” Since this means that the malware could collect personal or business data and initiate a large-scale destructive attack, Cisco’s recommendation was for owners of network-attached storage devices (NAS) to be especially wary of the malware. Cisco researchers were unable to determine how the compromised routers were infected, so officials are urging owners of all routers and NAS devices — not just those that were identified — to reboot. Cisco’s Talos Intelligence group has a complete report online that is available here.
According to the FBI statement, “The FBI recommends any owner of small office and home office routers reboot the devices to temporarily disrupt the malware and aid the potential identification of infected devices. Owners are advised to consider disabling remote management settings on devices and secure with strong passwords and encryption when enabled. Network devices should be upgraded to the latest available versions of firmware.”
The image below, from Cisco, shows that there are three stages to VPNFilter: a persistent stage 1 and non-persistent stages 2 and 3. Rebooting clears out stages 2 and 3 to mitigate most issues from the malware. The FBI seized a domain used by the malware creators to deliver stages 2 and 3 of the attack, so those stages of the malware can’t survive a reboot.
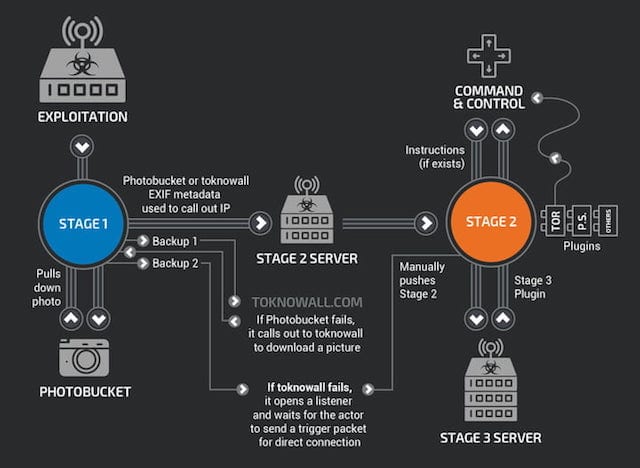
The DOJ issued a warning similar to that from the FBI: “Owners of SOHO and NAS devices that may be infected should reboot their devices as soon as possible, temporarily eliminating the second-stage malware and causing the first-stage malware on their device to call out for instructions. Although devices will remain vulnerable to reinfection with the second-stage malware while connected to the Internet, these efforts maximize opportunities to identify and remediate the infection worldwide in the time available before Sofacy actors learn of the vulnerability in their command-and-control infrastructure.”
Cisco has gone one step further, asking all users to perform a factory reset of their devices. Doing so even clears out stage 1 of the malware. If you have a Cisco router, visit the company’s wireless support site for instructions on how to do a factory reset.













Thanks.
I notice that since June1 there have been several questions with no answers. I also looked for info on this with regard to Apple routers to no avail.
I have a Cox cable modem connected to a Time Capsule. Just the Tme Capsule, both or do nothing?
How about my Apple airport router ?
Service providers like Verizon could certainly write some code to reboot customer’s routers when they are idle. This could happen quite frequently, which would keep the malware disrupted.
Of course, Verizon has NOT notified their customers to do this…
Does this apply only to WIRELESS routers, or does this apply to wired (Ethernet) routers as well?