macOS Catalina has some interesting new features, including Screen Time and Sidecar, and new apps, including Music, Podcasts, and Apple TV, that essentially replace iTunes. But behind the scenes, macOS Catalina has a number of new security features designed to ensure the Mac remains a safe and secure environment, protecting users from exploits and malware without creating obstacles or placing limits on how you can use your Mac.
In this article, we’ll look at some of the security changes in macOS Catalina, and how they’ll affect users and developers.
macOS Catalina Security
Catalina’s security is spread across a number of areas, including:
- System security: Protects the foundation of the operating system.
- Data protection: Protects user data from unauthorized access.
- App security: Protects a Mac and its users from malware, and ensures apps run in a secure environment.
- Device management: Prevents unauthorized use of Macs (and other Apple devices), and allows data to be wiped on lost or stolen devices.
The security features included with macOS Catalina are designed to address one or more of the categories noted above.
System Security
There are a number of changes to the system designed to protect the integrity of the system and keep it safe from malware and wayward apps.
Read-Only System Volume: The startup drive is no longer a single volume; it’s now made up of two APFS volumes: a read-only system volume that contains the macOS, and a data volume that contains all of the user’s data, documents, pictures, user installed apps, just about anything that isn’t part of the macOS.
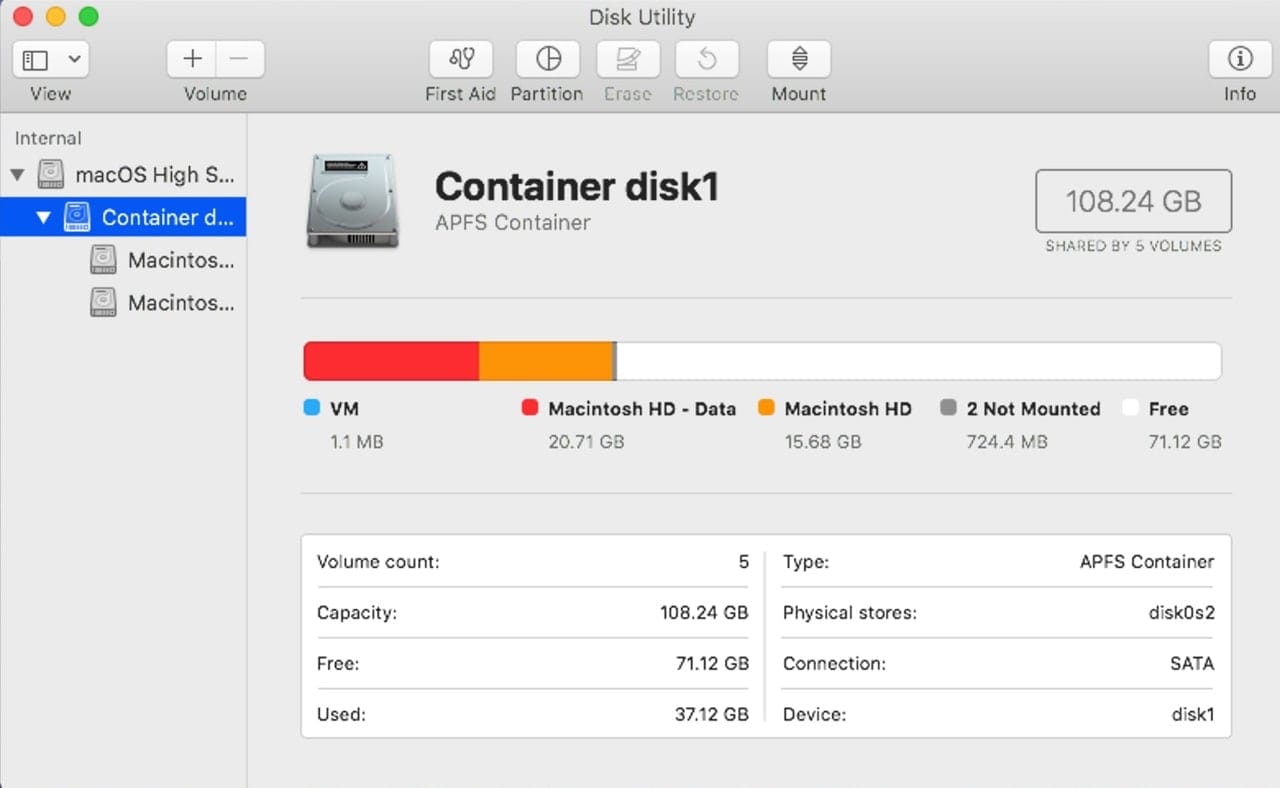
By mounting the system volume as read-only, it’s nearly impossible for any type of malware, or for that matter, a wayward app, to change or compromise the system.
One way to think of this is as an enhancement to SIP (System Integrity Protection), which was used in previous versions of the OS to protect specific directories used by the OS. With Catalina, the entire system volume is protected; not just individual directories.
The read-only system volume prevents any changes to the system, other than those delivered by signed code from Apple, which can perform updates to the volume.
The read-only system volume and the data volume are part of an APFS volume group and appear as a single volume in the Finder. The Mac performs this trick using a new type of file linking system known as firmlinks. Firmlinks have many uses, but one that is used in Catalina is to map various files and directories on the system volume to writeable shadow locations on the data volume.
The read-only system volume and writable data volume, along with the new firmlinks, have implications to how backup systems perform. Make sure your preferred backup system is macOS Catalina-ready before committing to using Catalina beyond a testing or evaluation phase.
Kernel Extensions: Kexts (kernel extensions) are slowly being replaced with system extensions, which will exist outside of the protected system volume. Catalina will be the last macOS that will run existing kexts. Developers working on new drivers (a common use for kexts) will need to use system extensions, which run in user space instead of within the system kernel.
Existing kernel extensions that were installed prior to the installation of Catalina will be able to run, though they may be subject to User-Approved Kernel Extension Loading. Even if you were using a kext previously, you may need to obtain an approval the first time it’s loaded.
Installing kexts or system extensions will likely require a restart of the Mac.
Moving kexts to system extensions that run as separate processes outside of the system ensures that if something is wrong with an extension, either from poor design or an attack from malware, the system itself is not affected.
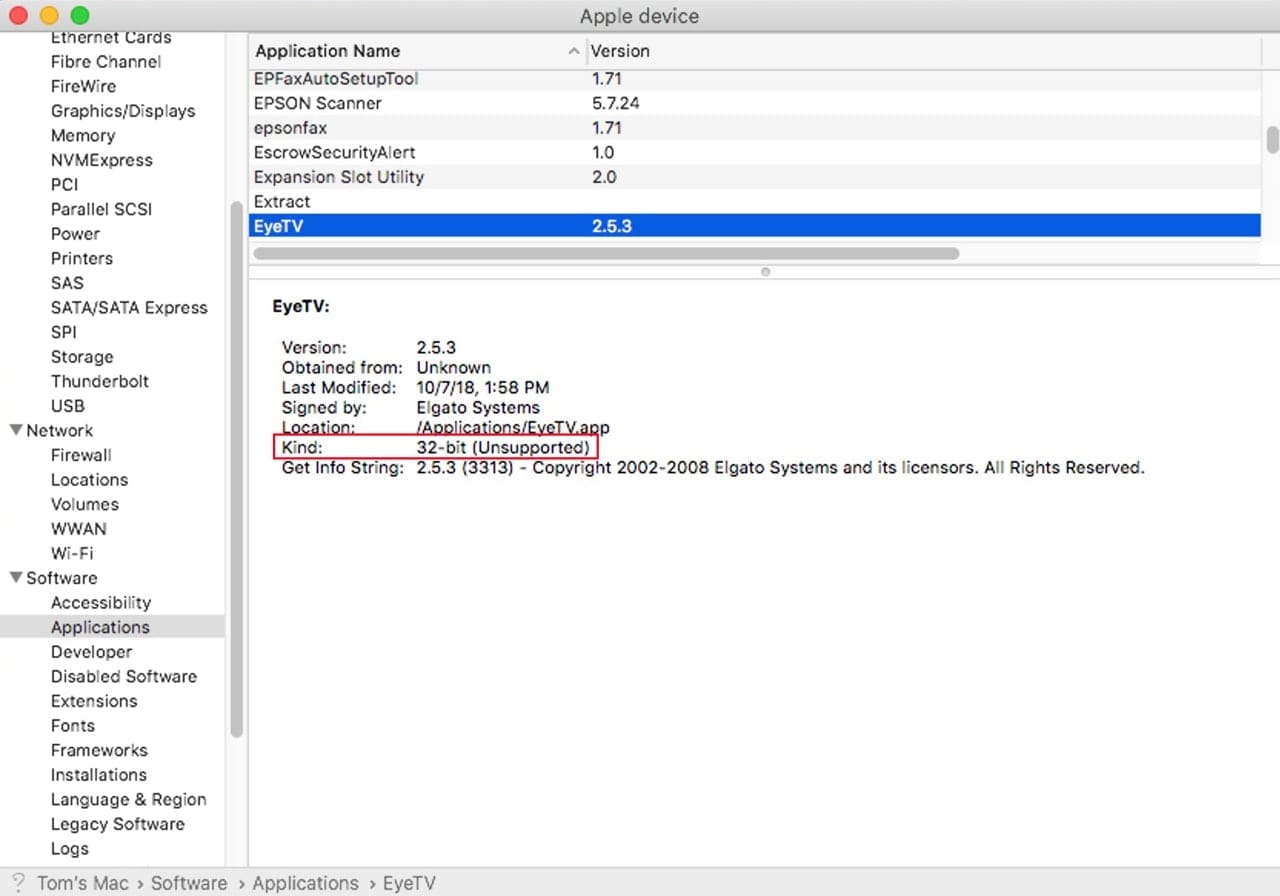
32-bit Apps/i386 code: As expected, Catalina has removed all support for 32-bit code. This means a number of older apps that have not been updated to 64-bit will cease to run. You can check if your existing apps are 64 bit using the instructions in How to Tell If Your Mac’s Software Is 32 or 64-Bit. You can also try Go64, a free app from St. Clair Software that will find 32-bit apps and locate upgrade information for them.
App Security
In the default configuration of the system, apps and services you’ve downloaded to your Mac must pass through a number of tests to ensure they’re malware free, and from known developers.
You can still run apps that don’t meet the security requirements, but it will require you to make a change or two to the Gatekeeper default settings.
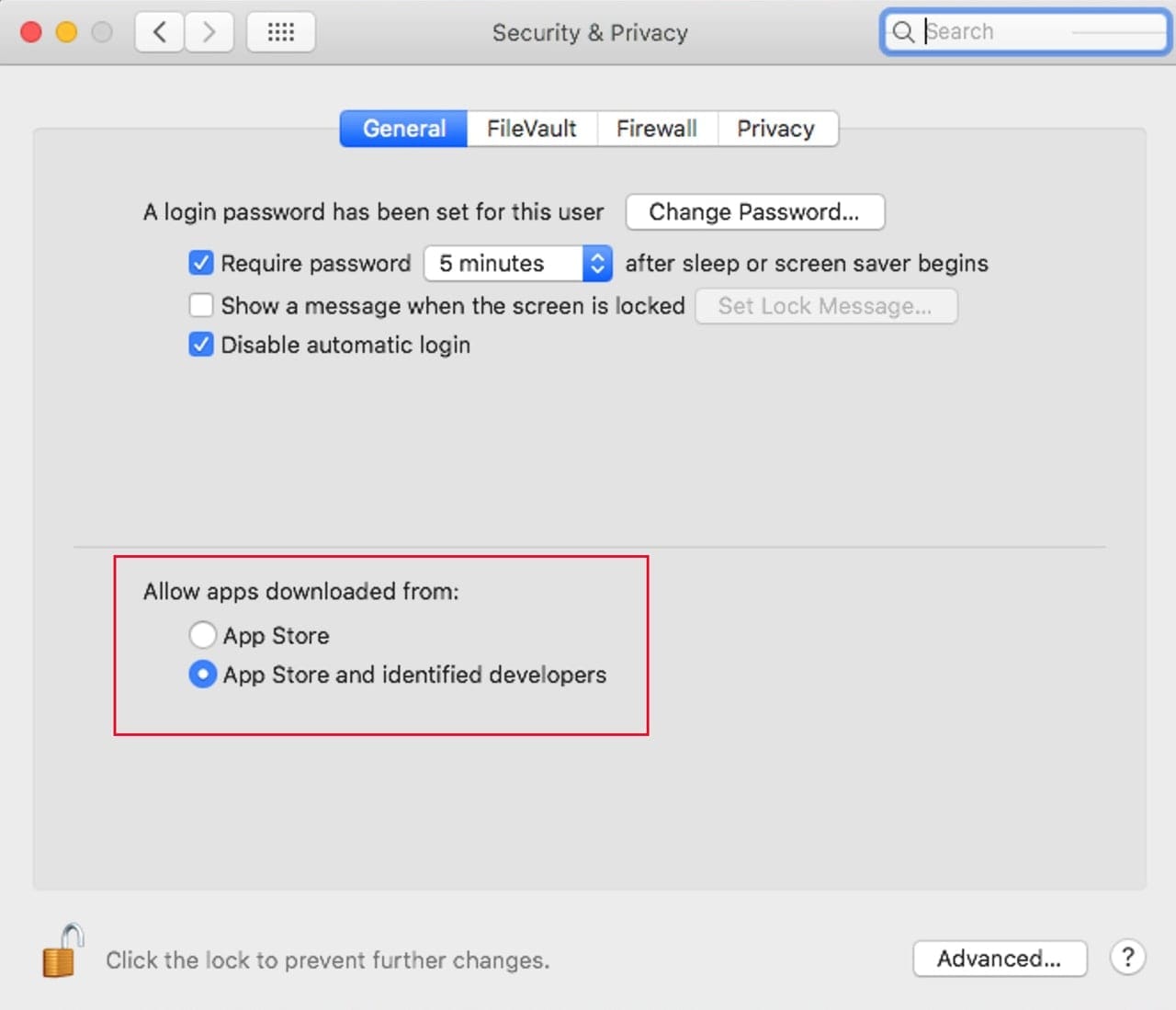
Gatekeeper: On the surface, there doesn’t seem to be too much changed in Gatekeeper. But on the inside, Gatekeeper has been enhanced dramatically. It can still be set to allow only apps from the App Store, or from the App Store and identified developers; you can also use a Terminal command to enable running apps from any source.
But now Gatekeeper will perform a scan of apps for both a valid signature, and to check for any known malicious content. This enhanced check is performed at random intervals and is designed to make sure that an app has not been tampered with after it was installed on your Mac.
Notarization: Developers have optionally been able to notarize their apps, essentially using an automated set of tools supplied by Apple to scan the app for malicious content before it becomes available for distribution. With Catalina, notarization becomes mandatory.
Data Protection
Apps and services need to behave in an expected manner. Apps should not be attempting to access user data or hardware and peripherals without specific permissions given by the user.
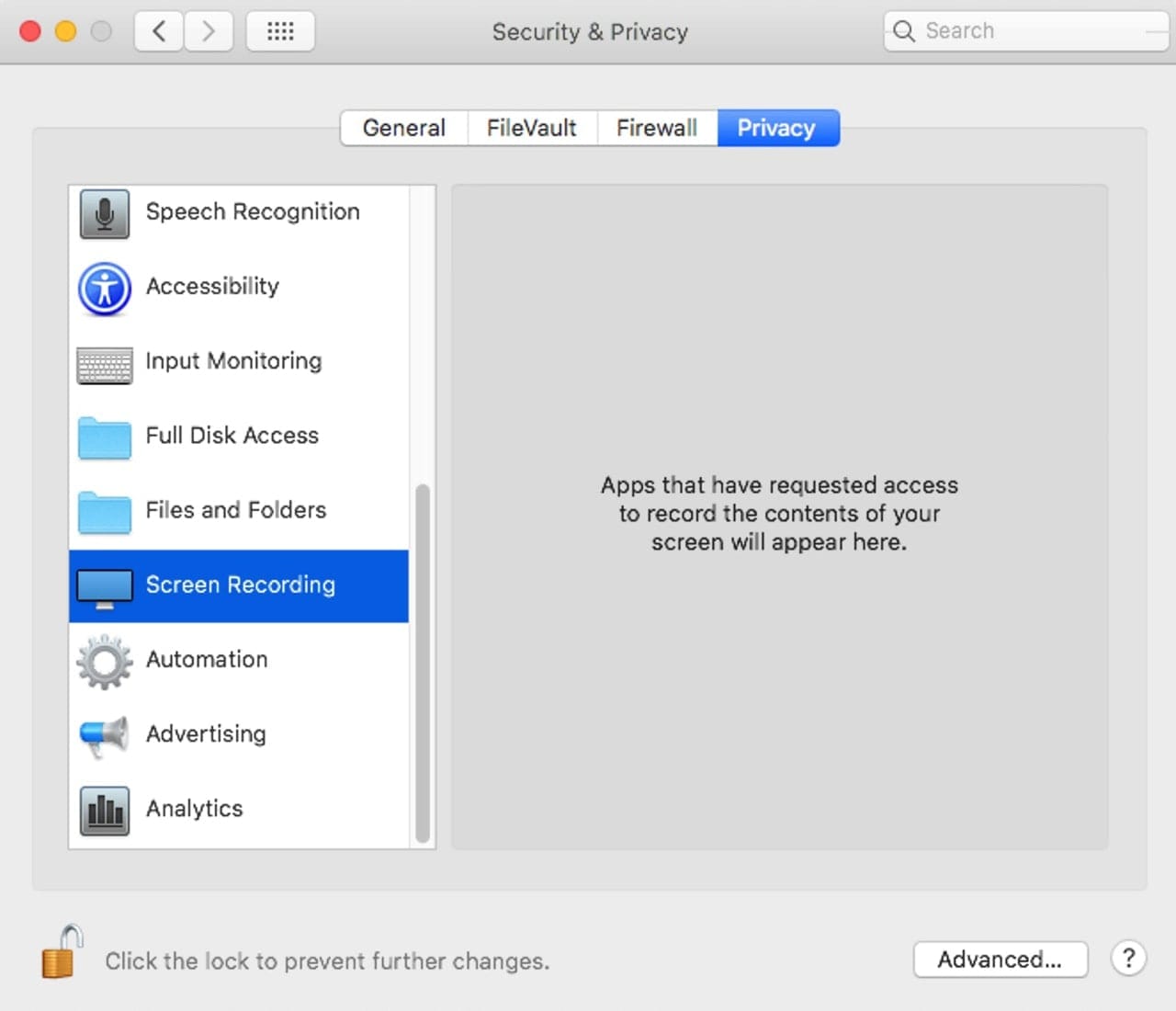
User Data Protection: The Mac already had a form of user protection, requiring you to approve apps that wish to access your camera or microphone. Catalina expands on this by requiring user permission for recording the screen or keyboard.
Besides asking permission for using devices, user protection will also ask if an app wishes to access sensitive data, such as contacts, calendar, and photos, or wants to access any number of file system locations, such as downloads, trash, the desktop, documents, iCloud drive, even most third-party cloud storage systems.
The Security & Privacy system preferences will keep track of which apps and services you’ve allowed access to, letting you revoke access at anytime.
Sign in With Apple: Apple is stepping up to compete with the popular Sign in with Google or Facebook services that seem to pop up everywhere you go on the web. Apple, of course, takes the concept to a better place.
Apple’s sign-in service is attractive because it promises a higher level of privacy and security than services from Google and Facebook, whose primary goal is to collect data from its users for its ad businesses.
Apple isn’t in the ad business and promises that information will not be used to sell ads or to track you. In addition, third-party systems using the Apple sign-in service won’t receive personal information, other than any
However, Apple goes another step further and offers to hide your real email address and use a throw away address generated by Apple. If you choose this route, the third party will be given an address such as 43a3cfb2ea@privaterelay.appleid.com. Mail sent by a third party will be forwarded by Apple to your iCloud email address (or the one registered with your Apple ID). You can interact using the cloaked email address without ever revealing your real one to the third-party service.
Sender Blocking in Mail: It’s nice to see Apple giving some attention to the Mac’s Mail app. In Catalina, you can block a sender that may be spamming your inbox, trying to acquire personal information via phishing, or just someone you don’t wish to see cluttering up your inbox anymore.
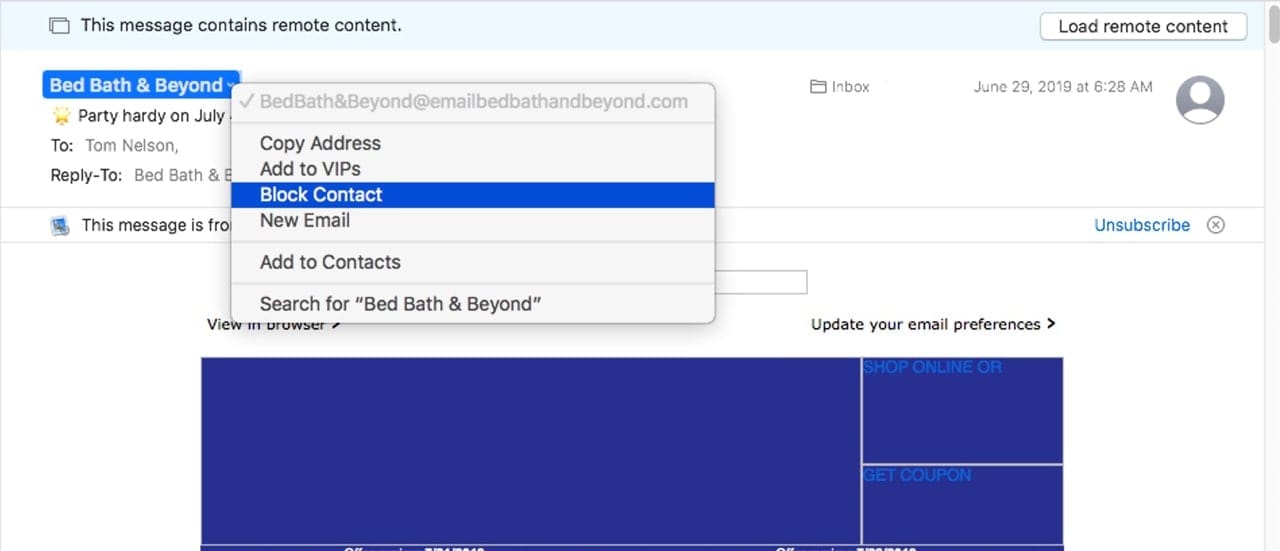
Blocking a sender is performed by selecting the sender’s name in an email’s header, and then selecting Block.
Device Management
You should be able to secure your Mac if it’s lost or stolen, and, hopefully, be able to locate the missing device.
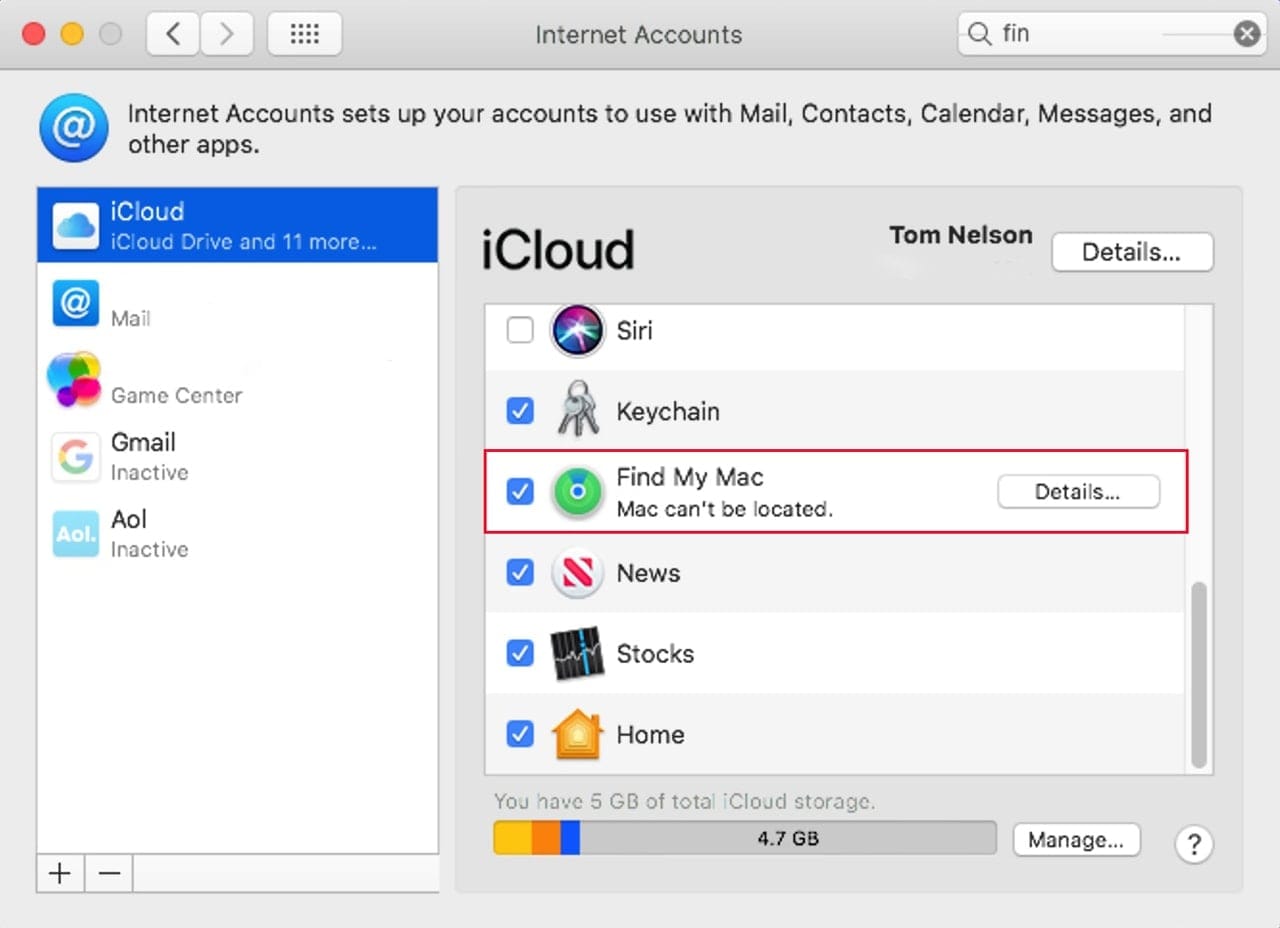
Activation Lock: If your Mac is configured with a T2 processor, macOS Catalina supports Activation Lock, which allows you to erase or deactivate a lost or stolen Mac, preventing anyone from being able to use the device. Should you regain possession of your Mac, you can use Activation Lock to reactivate the Mac, though any erased data will still be missing.
Find My Mac: Although not a new feature, Find My Mac has gained functionality that can allow you to locate a lost Mac even if the Mac is asleep. Find My Mac can now make use of Bluetooth to find other Apple devices nearby, and forward an encrypted data packet to Apple that contains your Mac’s current location. This information can then be accessed by the owner, from his or her iCloud account.
Wrap Up
There are a number of new security-related features in macOS Catalina; I only looked at the 10 I thought would be of the most interest to our readers. If you’re a developer, you’ll likely have quite a different list for your top 10 changes.
I hope this list will help you anticipate what changes will be coming when you decide it’s time to upgrade to macOS Catalina. What changes in macOS Catalina are you most concerned about, or looking forward to? Let us know in the comments, below.








Do all my Applescript Apps and my Shell Scripts run under Catalina as they did in previous OSes? If not, what needs to be done to achieve this?
Nice article. Thanks for the insights.
To make this more complete regarding your first point, there are actually 3 more partitions that make up the macOS “drive”. They include the VM partition, shown in your picture, and pre-boot and Recovery partitions, simply listed as “2 not mounted” in your picture.
The VM and pre-boot partitions are part of making macOS boot and run. The Recovery partition is where Apple stores the Mac OS Recovery tools, from where you can re-install macOS or run Disk Utility and perform other diagnostics.
Note that the last 2 partitions are created automatically as part of a macOS install but the VM partition is actually created by macOS after the first install or boot of macOS.
You can actually see those partitions using the Terminal app by typing diskutil list.
Looking forward to APFS being really a finished complete product:
– Time Machine 2 supporting making backups in APFS disks.
– Apple releasing full documentation about how to write to APFS disks (as they released by September 2018 about how to read APFS disks), so that developers like Alsoft can release DiskWarrior 6 to rebuild directory of APFS disks (safety net).
Agreed. They also need to update Disk Utilities to better support APFS. Creating disk images is a nightmare….
Just spent days trying to get it to create image of existing drive. Many errors, many “resource is busy”, many faulty images that can be used to restore anything.
Turns out the ONLY way to it reliably with their tool is muti step:
1. create new BLANK disk image with Read/Write privileges
2. use “Restore” to clone drive to new image
3. Convert the new image to Compressed format to be able to use the image to perform restores to another drive.
All this should all be done in one step, like it has always worked.
BTW, also not looking forward to losing 32-bit support. Still have some old non-replaceable tools that will die (or I could run them in a VM but that’s extra hassle to set up).
That is my plan. Am going to run a number of 32-bit apps in a VM using Parallels and macOS High Sierra.
Tom
Awesome. Many thanks!