 If your Mac seems to suddenly be running hot, with the fans making more noise than usual, your battery runtime has taken a nosedive, or you’ve noticed that your Mac seems to be slowing down, you may be experiencing the effects of cryptojacking.
If your Mac seems to suddenly be running hot, with the fans making more noise than usual, your battery runtime has taken a nosedive, or you’ve noticed that your Mac seems to be slowing down, you may be experiencing the effects of cryptojacking.
Of course, there are plenty of other reasons why your Mac could be misbehaving as outlined above; hot summer days can make your Mac run its fans at a higher rate, battery runtime can be affected by the type of processes you’re running, such as video or audio processing, and the Mac’s processors may simply be engaged in running multiple threads from multiple apps, keeping things a bit tied up.
But you could also be a victim of cryptojacking. In this Rocket Yard Guide, we’re going to take a look at cryptocurrency, how it’s mined, and how it may be affecting your Mac.
What Is Cryptojacking? The New, Friendlier Malware
Cryptojacking is a somewhat new way for nefarious individuals to make use of your Mac’s processing power for their own gain. With cryptojacking, the gain is in the acquisition of cryptocurrency coins by having your Mac solve complex mathematical problems. Each solved problem is worth some number of coins or fractions of coins in the cryptocurrency being mined.
Mining for money using your Mac’s hardware without your consent is commonly referred to as cryptojacking. Coin mining is probably best known as the way to acquire Bitcoins, a popular cryptocurrency that has been in use for a number of years. In the early days of coin mining, the tasks a computer had to perform to generate a coin were easy enough that a moderately outfitted personal computer could perform the tasks in a reasonable amount of time. As cryptocurrency become more popular, the difficulty of the problems that needed to be solved increased dramatically, to the point where multiple specially designed computer rigs were being used together to solve the problems and generate cryptocoins in a reasonable timeframe.
As the various cryptocurrencies gained support, the mining of the coins became more and more difficult, so that the days of someone using an average personal computer to solve problems and generate coins went by the wayside. Nowadays, the mining, a common term for solving the problems and generating the coins, is being performed by highly advanced, dedicated mining rigs, or through distributed computing systems that use a large number of individual computers, each working on a piece of the puzzle.
It’s this last mining rig type that has spawned the growth of cryptojacking, using computers that have had mining software installed without the consent of the owner to hijack the computer’s processing power to mine for coins.
Types of Cryptojacking
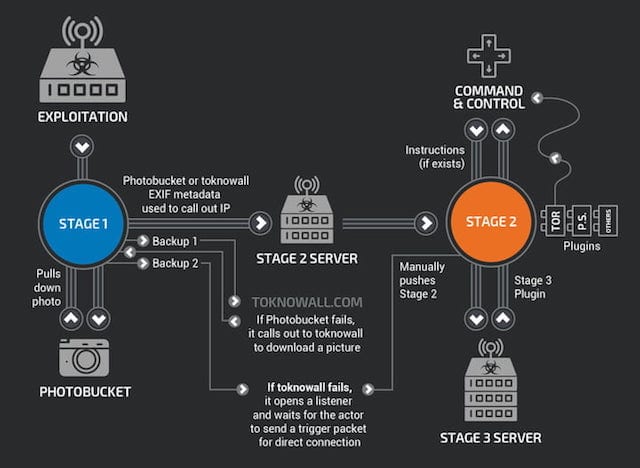
Cryptojackers use two common methods of manipulating a computer to run mining software. The first, and somewhat less common at the moment, is the old standard malware approach of using a Trojan app to install the mining app on an unsuspecting system. This usually takes the form of a mining app masquerading as another, more popular application. Once the app is downloaded and the installer run, the crypto miner is installed and starts mining for coins.
However, the most likely way for a Mac to run into cryptojacking is through a web browser. The software for mining cryptocurrency has been developed using JavaScript, which every web browser can run. Cryptojackers can insert the JavaScript code into a hacked website, or they can embed the JavaScript mining code within ads which are then placed on many websites.
All you need to do is visit one of these websites, and your Mac will start happily running the cryptocurrency mining code.
For the cryptojacker, using web-based infection has many advantages. It’s easy to do; while they can hack a website and insert the code, they can also just create an ad and place it with an ad service to have it distributed to many websites. Web-based cryptojacking also doesn’t require any type of enticement to get you to download and install a cryptojacking app; instead, the browser runs the mining code for as long as the webpage is open; no installation of code required.
How to Detect Cryptojacking on Your Mac
Cryptojacking is relatively new, and as such, most cryptojacking methods use similar JavaScript that runs within a browser page. The JavaScript attacks tend to quickly elevate CPU usage, allowing you to easily detect the intruder’s presence using the Mac’s built-in Activity Monitor app.
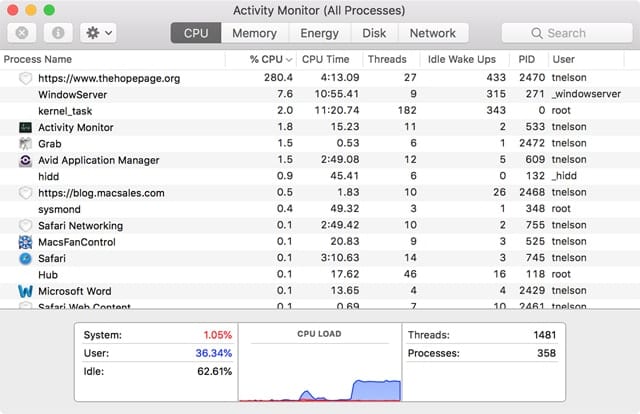
Launch Activity Monitor, located at /Applications/Utilities.
In the Activity Monitor window, select the CPU tab.
At the bottom of the window you’ll see the CPU load represented as a graph; you’ll also see the CPU load represented by percentage used by System, User, and Idle.
When you open your browser to a web page, you may see a slight bump in User CPU utilization as the page is loading, but after that, the CPU utilization will likely return to a normal range.
When you load a website where cryptojacking is occurring, you should see the CPU utilization rise quickly and stay in a high range as long as the web page remains loaded in the browser. Close the web page or quit the browser, and the CPU load should drop back to a normal level.
Keeping an Activity Monitor window open on the desktop can get in the way of the work you need to be doing. Instead, you can set the Activity Monitor’s Dock icon to display the CPU usage history dynamically.
From Activity Monitor’s View menu, select Dock Icon, Show CPU History.
You can now close the Activity Monitor window, and the Dock icon will still display CPU utilization.
If you would like to see an example of cryptocurrency mining and how it affects CPU utilization, you can load TheHopepage.org in your web browser. This page, run by the UNICEF organization, will ask your permission to donate some of your Mac’s computing horsepower to generate cryptocurrency to be used to help supply water, food, and vaccines to children. This is an example of cryptocurrency mining being used with your permission for a stated goal. You can even set the percentage of CPU power you wish to allow the site to use. Once you close the page, the mining will stop.
Unlike the UNICEF site we used for demonstration, cryptojacking sites use your processing power without your permission and for unknown goals.
How to Prevent Cryptojacking
Because browser-based cryptojacking uses JavaScript, you can use one of the many ad-blocking browser extensions. This type of ad blocker will help prevent cryptojacking that is being delivered via ads embedded in websites.
Some browser extensions, such as Adblock, Adblock Plus, No Coin, and MinerBlock, have support for preventing cryptojacking by using a list of known websites that employ cryptojacking tactics. If you use an ad blocker, be sure to check its settings to see if a cryptojacking prevention feature has been added.
Another method to block cryptojacking is to use an anti-malware app, such as Malwarebytes (premium version), that has cryptojacking detection capabilities and actively blocks known cryptojacking sites and services, such as Coinhive. Coinhive is a service that offers cryptocurrency miners in the form of JavaScript code to other websites in exchange for a cut of all the cryptocurrency a site generates. Many of the websites actively employing cryptojacking make use of the Coinhive service.
Less common, at least for the Mac community, are cryptojacking apps that run independent of a web browser. One of the original miner apps for the Mac went by the names DevilRobber, Coinbitminer, and Miner-D. Back in 2011, Apple released a security update to thwart how these cryptominers communicated with a remote server.
Since then, hidden mining apps have been few and far between on the Mac, with perhaps the only recent sighting being an app going by the name mshelper. How mshelper is distributed isn’t fully known, though it appears to be attached to other apps a user may download, such as a Flash updater.
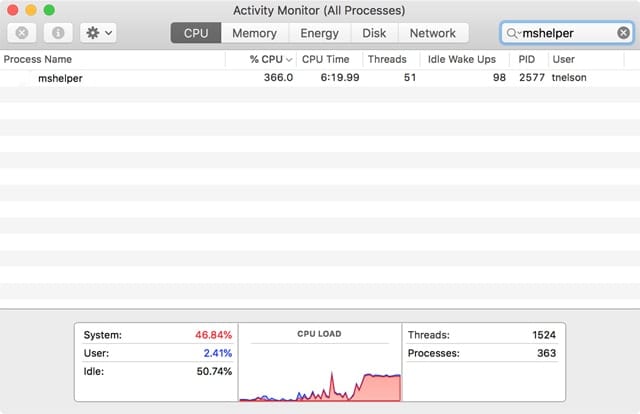
Most anti-malware apps can detect and remove mshelper, but you can also check for its presence using Activity Monitor:
Launch Activity Monitor and select the CPU tab.
In the Search field, enter mshelper and press return.
If the app is installed on your Mac, it will be displayed in the list. If nothing shows up, your Mac doesn’t have the cryptomining app mshelper installed.
If it is present, select the mshelper app in the Activity Monitor window, then click the Force Process to Quit button, located at the top left of the Activity Monitor toolbar (it looks like a circle with an X through it).
Once the mshelper has quit, you need to remove two files:
Use the Finder to navigate to /Library/LaunchDaemons/ and delete the file named: com.pplauncher.plist.
Use the Finder to navigate to /Library/Application Support/ and delete the file named: pplauncher.
Both of these files are in the Library folder on the startup drive, and not the individual users’ Library folder.
Cryptojacking’s Other Side
I mentioned earlier that cryptojacking was the new, friendlier malware. That’s because cryptojacking doesn’t permanently harm your computer, nor does it collect personal information or attempt to encrypt your data to ransom it back to you.
Interestingly, ransomware-based attacks have fallen considerably since the rise of cryptojacking. This may be because cryptojacking is easy to perform and is difficult to trace back to the originator, making it much less risky to attempt.
Also interestingly, a few web services have experimented with using open, aboveboard, and voluntary cryptomining to replace or reduce ads being shown on a website. If you’re a Salon reader, you may have already seen the opt-in option for cryptomining to replace ads.
Salon’s use of cryptomining is a beta and may never actually replace ad revenue, but it’s interesting to see cryptomining being used in ways other than stealing processing performance with cryptojacking.













this only works for Safari, which shows each webpage. Firefox bundles them together.
Can someone reply to Mitch’s question below? I think it’s vitally important that we know whether or not these types of exploits are possible in iOS!
Many thanks,
John
Wouldn’t this technique work in iOS, since it just uses JavaScript? I noticed a family iPad getting really hot and Settings, Battery showed Safari being the dominant app used more than any other app. Perhaps a follow up on which iOS content blockers prevent crypto mining?